How Platform Teams can enable developers to use their preferred Kubernetes Tools¶
There are cases where developers may prefer to use tools on their laptops such as Lens Desktop to visualize resources and interact with Kubernetes clusters. The use of a desktop based app such as Lens can be a better user experience for developers over the Kubectl CLI.
In this blog, we will describe how Platform Teams can use Rafay’s Zero-Trust Access service to enable developers to use popular Kubernetes visualization apps to troubleshoot their applications. Watch a video showing how a developer can use Lens Desktop with Rafay's Zero Trust Kubectl Access service to securely and remotely access Kubernetes clusters.
Challenges¶
Platform teams have the onus of enabling developers to use such tooling while ensuring there are sufficient guardrails in place. The challenges that Platform teams typically run into are threefold:
- Securely authenticating users: this ideally needs to be integrated with the organization’s Identity Provider (IDP) such as Okta, Azure AD etc.
- Role based access control (RBAC): relates to the ability to centralize this with a “least privilege” security model and being able to do it at scale across clusters and 100s of developers
- Securing access to KubeAPI servers: need to manually manage access to each cluster using jump hosts or VPNs, and build custom tooling to audit and map all actions performed to a user’s identity – all of which which is error-prone and increases the risk of breaches as the number of clusters grows
Important
Users need to know that although tools like Lens Desktop are free to download, they are not freeware. Click to view details about their pricing.
Typical Sequence¶
The sequence diagram shows how a developer can use Lens Desktop with Rafay's Zero Trust Kubectl Access service.
sequenceDiagram
autonumber
Developer--> Lens Desktop: User sets up Lens Desktop
Developer->> Rafay: User authenticates via Org IDP
Rafay->>Developer: User downloads consolidated kubeconfig
Developer->> Lens Desktop: User uploads kubeconfig
Lens Desktop-->>Rafay: Securely connects via Rafay's Zero-Trust proxy
Rafay-->> Remote Cluster: Proxy authenticates user, forwards the request
Note right of Rafay: Service account created with appropriate role/role binding
Lens Desktop-->>Remote Cluster: Subsequent user requests are forwarded by the proxy to the remote cluster
Note right of Developer: Audits for user actions are stored in Rafay's KOP
Remote Cluster->> Remote Cluster: Service account gets removed after configured inactive periodDeveloper downloads kubeconfig file from Rafay¶
- Developer authenticates against the organization’s IDP and logs into Rafay
- A consolidated kubeconfig file is available for the developer to download, the kubeconfig file reflects the access (clusters, role) that the Platform team has configured for the developer
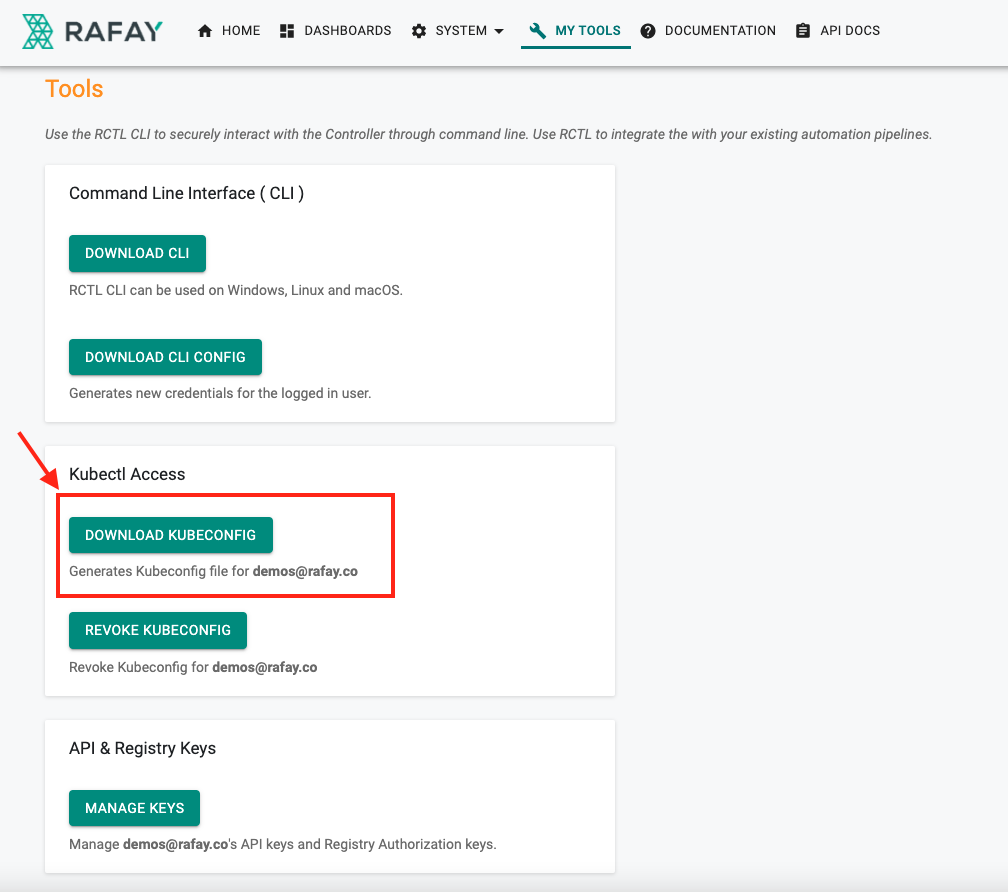
Developer provides the Rafay Zero Trust kubeconfig file to Lens Desktop¶
- Navigate to Clusters page within Lens Desktop, Select the “add from kubeconfig” option
- Paste from the kubeconfig file downloaded as part of the previous step
- “Successfully added clusters” message is displayed
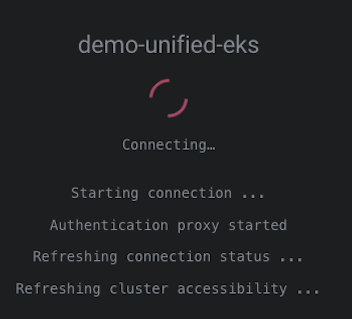
- Lens Desktop connects to the cluster securely through Rafay’s Zero-Trust Proxy and fetches the cluster information
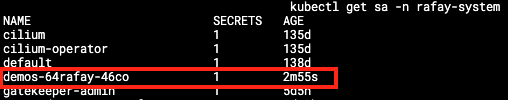
- A JIT service account is created for the user on the cluster with the appropriate role/role binding
Day 2 Operations¶
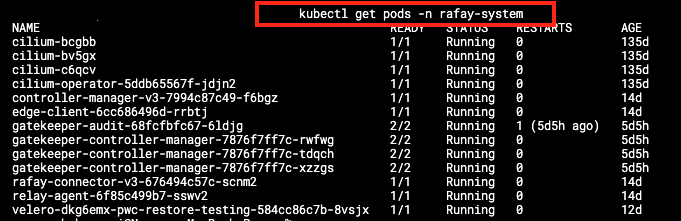
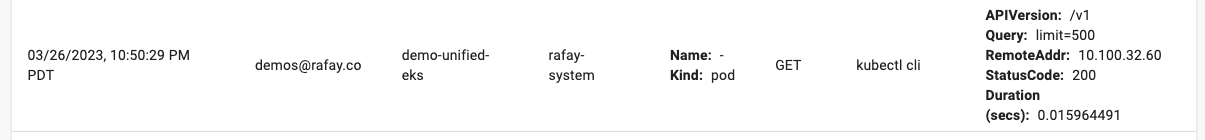
- A full audit trail is persisted for user actions within Rafay’s platform and is available in real time
- There may be cases where a user no longer requires kubectl access or the kubeconfig file may have been compromised (e.g., lost/stolen laptop). It is straightforward from within Rafay’s platform to revoke a specific user’s kubeconfig immediately. Note that this can be done centrally across clusters i.e., it is not required to do this cluster by cluster
- Platform teams can configure “idle time” for the ephemeral service accounts beyond which it is automatically de-provisioned. This ensures that there are no dangling service accounts on the cluster presenting a security risk
Conclusion¶
Rafay enables platform teams to integrate best practices across Secure Access, Kubernetes RBAC and SSO to enable a Zero-Trust model for K8s infrastructure.
| Challenge | How does Rafay help? |
|---|---|
| Securing access to KubeAPI servers | Rafay’s Zero-Trust architecture removes the need for customers to leverage a VPN solution/bastion server access model and/or open ports in firewalls |
| Managing Kubernetes RBAC | Rafay enables customers to centralize orchestration of access policies at scale across fleet of clusters |
| SSO integration | Rafay enables customers to integrate their IDP and have the user role/access determined by the group membership in the identity provider |
Learn More?¶
Sign up here for a free trial and try it out yourself. Get Started includes a number of hands-on exercises that will help you get familiar with capabilities of Rafay's Kubernetes Operations Platform.
