Control Plane
Amazon EKS is a managed service that makes it easy for users to run Kubernetes without installing and operating the Kubernetes control plane (i.e. master nodes).
As part of the service, AWS automatically provisions and scales the Kubernetes control plane, including the API servers and backend persistence layer, across multiple AWS availability zones for high availability and fault tolerance. Amazon EKS automatically detects and replaces unhealthy control plane nodes and provides patching for the control plane.
The AWS managed EKS control plane with the master nodes is provisioned in a separate AWS VPC that is attached to the user's VPC hosting the worker nodes. See architecture below.
EKS Control Plane¶
The Amazon EKS Control Plane is a "multi master" deployment with three masters operating in a HA configuration.
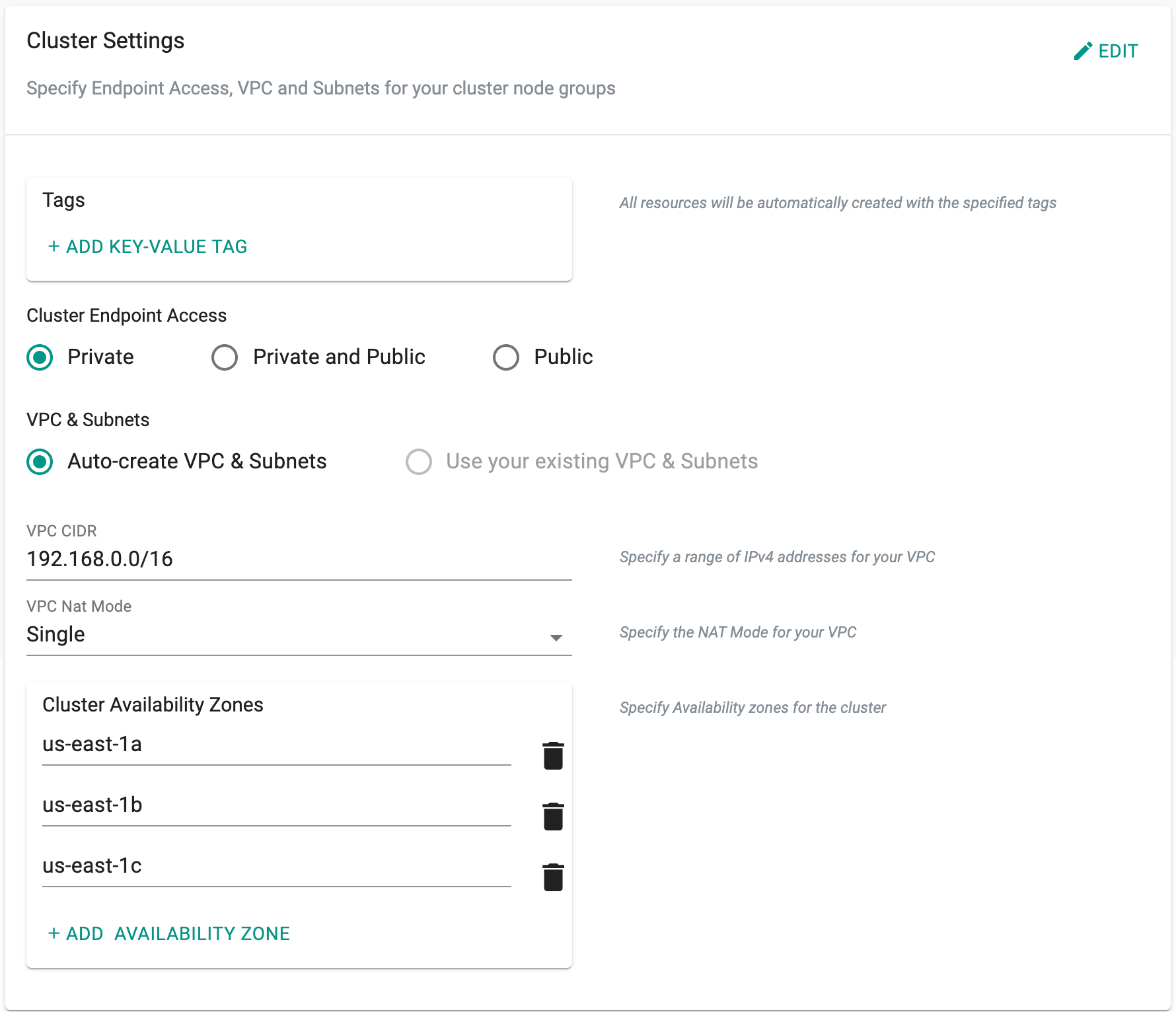
By default, three AZs are randomly selected in the user specified AWS region. Cluster admins can override the default and specify the AZs where they would like to provision the EKS Control Plane. Note that it is not possible to change this once the cluster has already been provisioned.
- Select Networking and Edit
- Enter three AZs in the selected region
For example, for this EKS cluster in the "us-east-1" region, we have selected "us-east-1a", "us-east-1b" and "us-east-1c" as the three AZs for the EKS Control Plane.
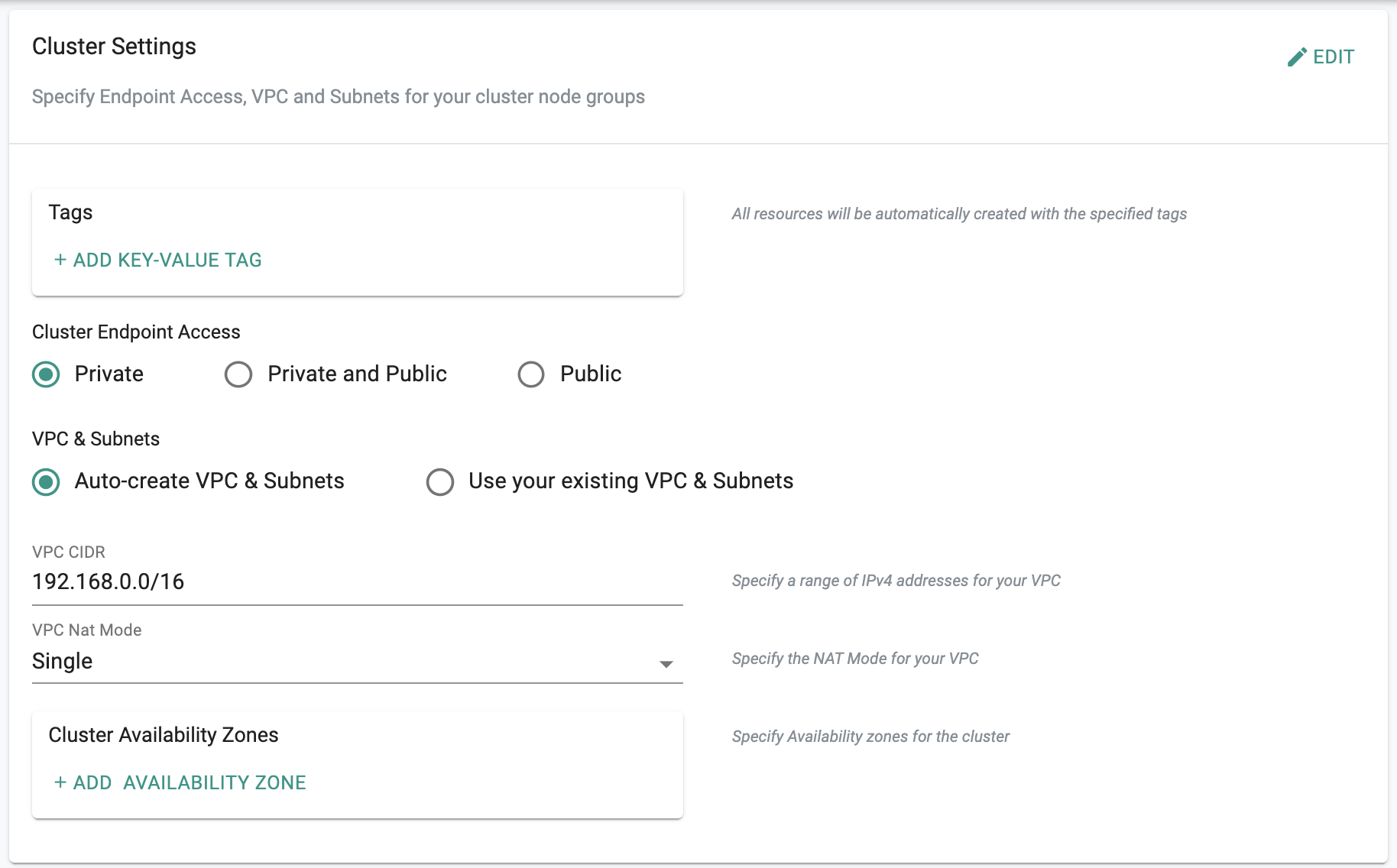
AWS Tags¶
Tagging in AWS is a best practice employed by many organizations. Specify "tags" here to make sure that all resources will be created in your AWS account with the configured tags.
Important
Amazon EKS may not supported in certain AZs. For example, "us-east-1e".
Private Access¶
Amazon EKS creates an endpoint for the managed Kubernetes API server that cluster administrators etc can communicate with it. Learn about Access Control for the EKS Cluster Endpoints.
By default, as a security best practice, the Controller provisions the EKS Control Plane so that the API server endpoint is Private i.e. secure and not visible on the Internet.
With this default configuration,
- All traffic to your cluster API server must originate from within your cluster's VPC or a connected network.
- All communication between the worker nodes and the API server stays within your VPC.
- Public access to your API server from the internet is disabled.
- Any kubectl commands must come from within the VPC or a connected network.
The Controller provides "Zero Trust Secure Access" to Kubernetes clusters under management.
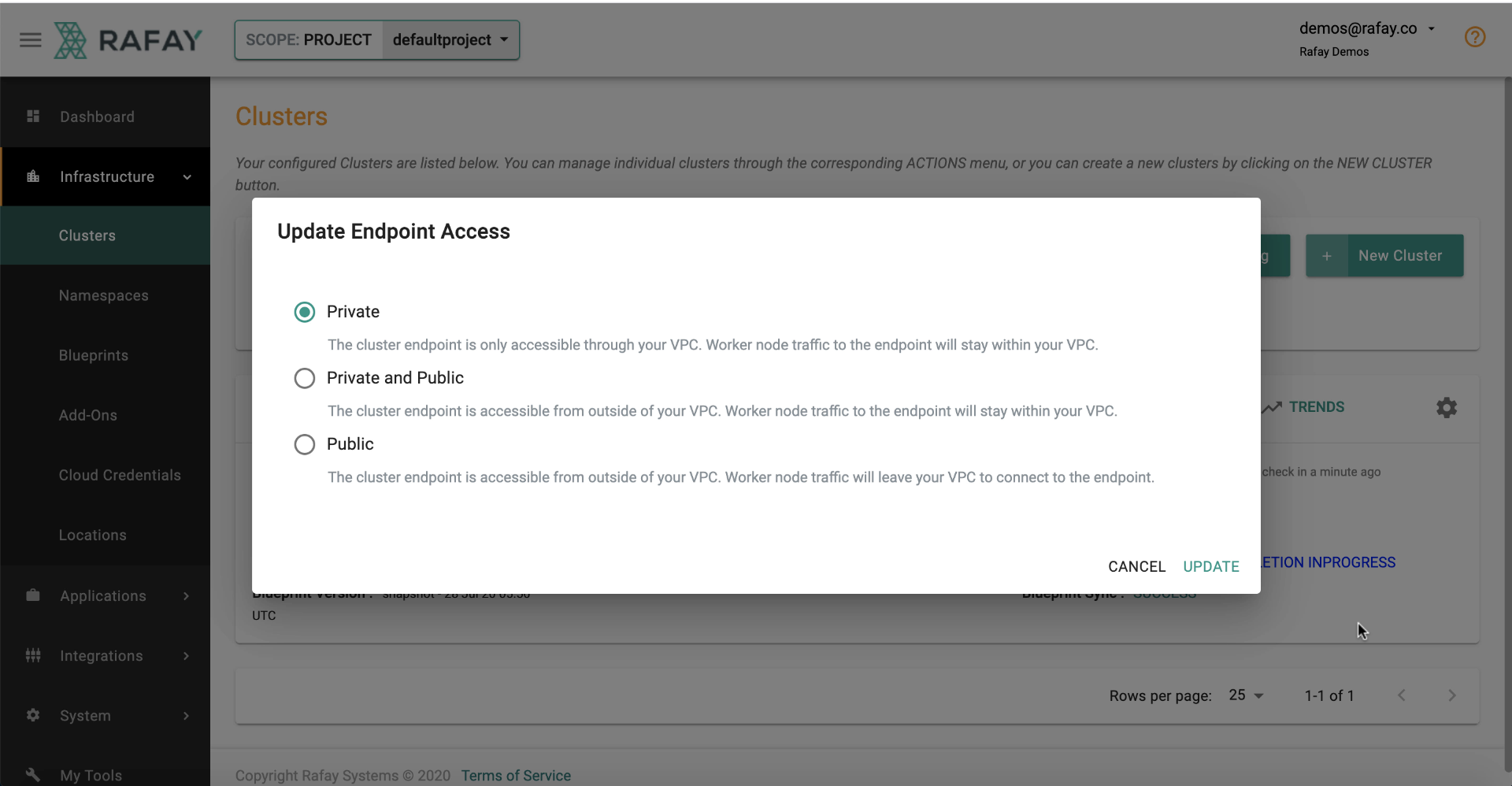
Updating Endpoint¶
Although possible, we strongly recommend to not change the default, secure setting for endpoint access (i.e. Private).
The Controller provides the means to update the endpoint type directly from the Console. If you need anything other than Private, we recommend that you limit the IP addresses that can access your API server from the Internet.
- Click on the gear option
- Select Update Endpoints
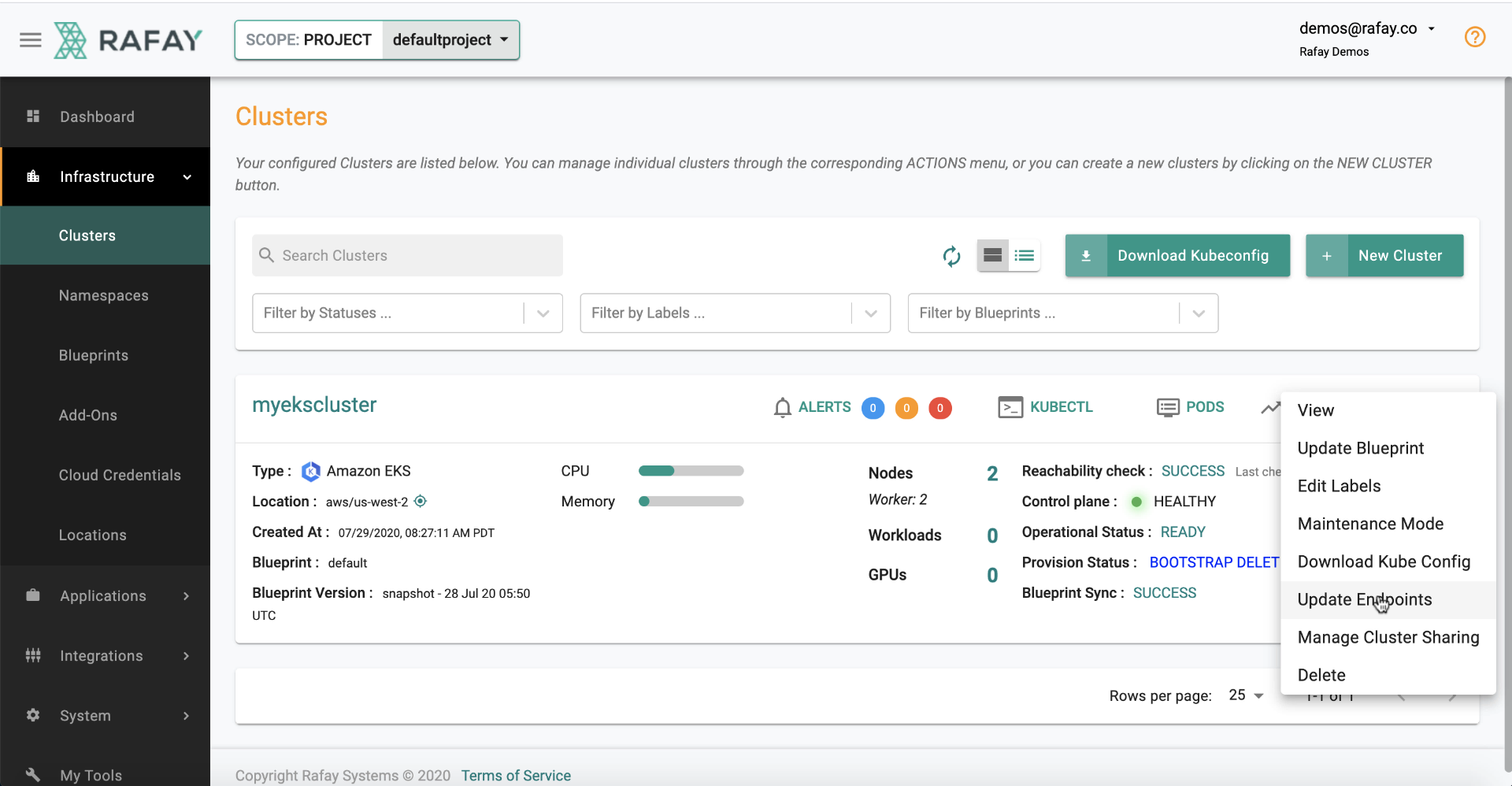
- Select type of access for Endpoint
- Update