Node Taints
The Kubernetes scheduler determines which nodes pods are scheduled on. In general, the scheduler is free to place a Pod on any node that satisfies the Pod's CPU, memory, and custom resource requirements.
In some scenarios, users may want to exercise some control over which pods can run on a particular pool of nodes. Taints are used to repel Pods from specific nodes. Instead of applying the label to a node, users can apply a taint that tells a scheduler to repel Pods from this node if it does not match the taint. Only those Pods that have a toleration for the taint can be let into the node with that taint.
- A node taint lets you mark a node so that the scheduler avoids or prevents using it for certain pods.
- Node taints are key-value pairs associated with an effect.
Effects¶
Here are the available effects:
NoSchedule¶
Pods that do not tolerate this taint are not scheduled on the node; existing Pods are not evicted from the node.
PreferNoSchedule¶
Kubernetes avoids scheduling Pods that do not tolerate this taint onto the node.
NoExecute¶
Pod is evicted from the node if it is already running on the node, and is not scheduled onto the node if it is not yet running on the node.
Important
Some system Pods such as kube-proxy and fluentd tolerate all NoExecute and NoSchedule taints, and will not be evicted.
Typical Use Cases¶
In general, taints and tolerations support the following use cases:
Dedicated nodes¶
Users can use a combination of node affinity and taints/tolerations to create dedicated nodes. For example, you can limit the number of nodes onto which to schedule Pods by using labels and node affinity, apply taints to these nodes, and then add corresponding tolerations to the Pods to schedule them on those particular nodes.
Special hardware¶
If you have nodes with special hardware (e.g GPUs) you want to repel Pods that do not need this hardware and attract Pods that do need it. This can be done by tainting the nodes that have the specialized hardware (e.g. kubectl taint nodes nodename special=true:NoSchedule ) and adding corresponding toleration to Pods that must use this special hardware.
Taint-based Evictions¶
New Kubernetes versions allow configuring per-Pod eviction behavior on nodes that experience problems.
View Node Taints¶
To view labels associated with a node in a cluster,
- Click on Cluster
- Select the Nodes tab
- Select the specific node and expand it
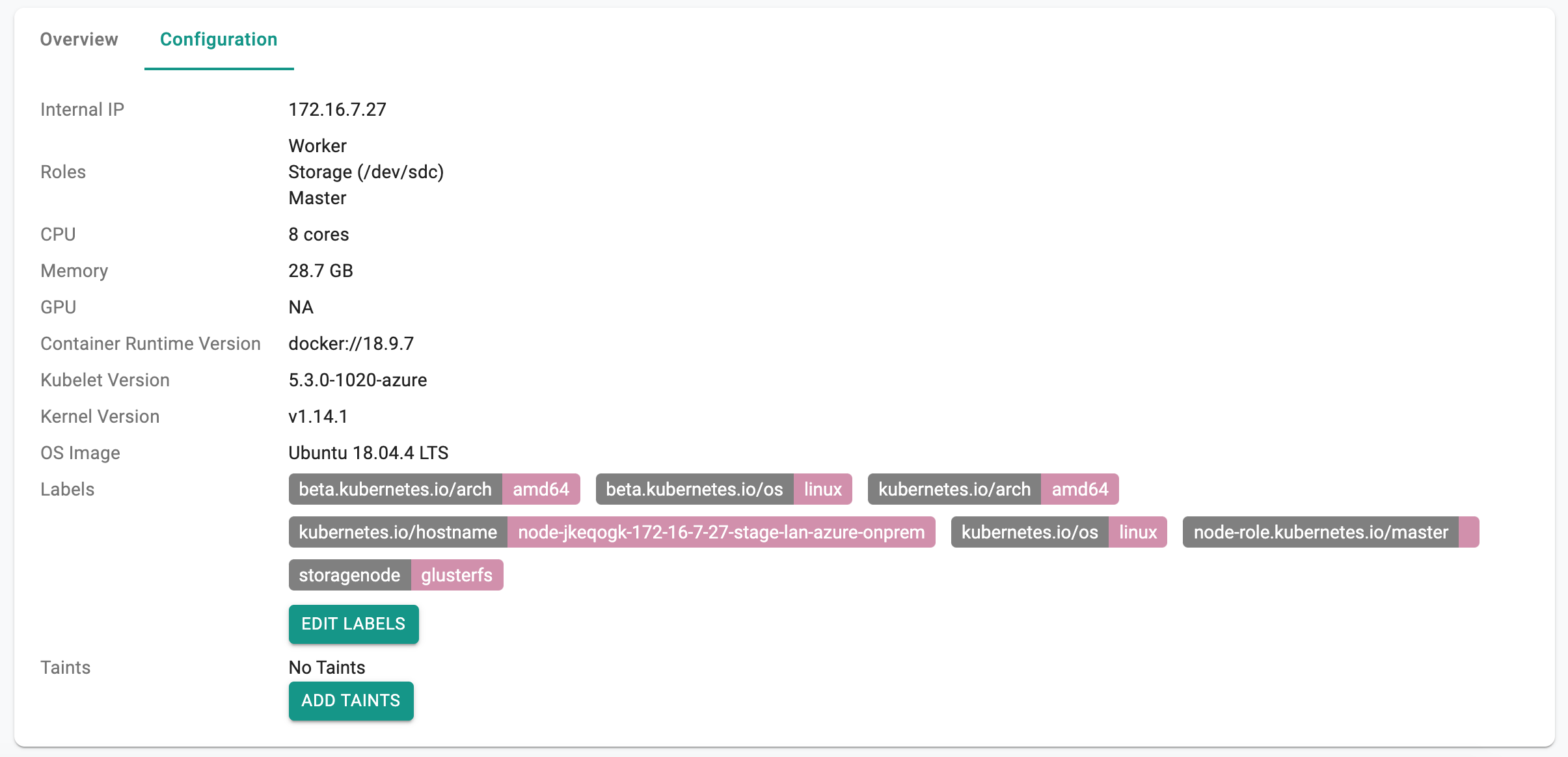
By default, there are no taints applied to any nodes.
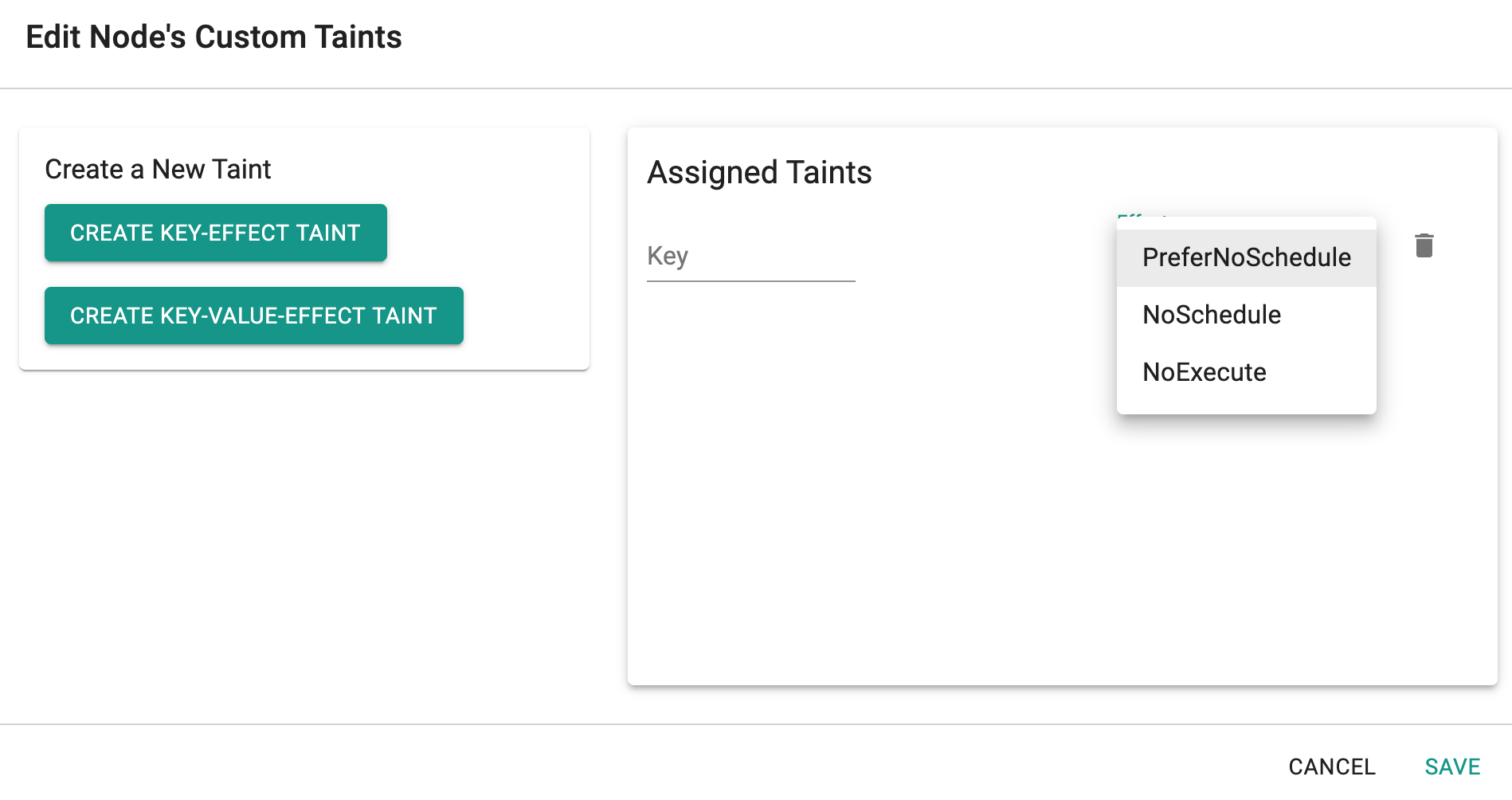
Add/Remove Node Taints¶
To add/remove taints associated with a node in a cluster,
- Click on Cluster
- Select the Nodes tab
- Select the specific node and expand it
- Click on "Edit Taints" and follow instructions
KubeCTL¶
To view taints associated with a node in a cluster using KubeCTL, in the Web Console, open the browser based KubeCTL shell and type the following command.
kubectl describe nodes <name of host>