Overview
Worker nodes in an Amazon EKS Cluster will operate either in a public or a private subnet. If the subnet’s traffic does not have a default route through an Internet Gateway, this subnet is considered to be private. There are three ways to configure the VPC for your Amazon EKS cluster:
Only Public Subnets Worker Nodes and Ingress resources (like load balancers) all are instantiated in the same public subnets.
Only Public and Private Subnets Worker Nodes are instantiated in private subnets and ingress resources (like load balancers) are instantiated in the public subnets.
Only Private Subnets There are no public ingress resources as this configuration is only used for workloads that do not need to receive any communications from the public internet.
Defaults¶
If nothing is specified, Rafay will automatically create a new VPC and required subnets with the following defaults. Cluster administrators can optionally override these defaults.
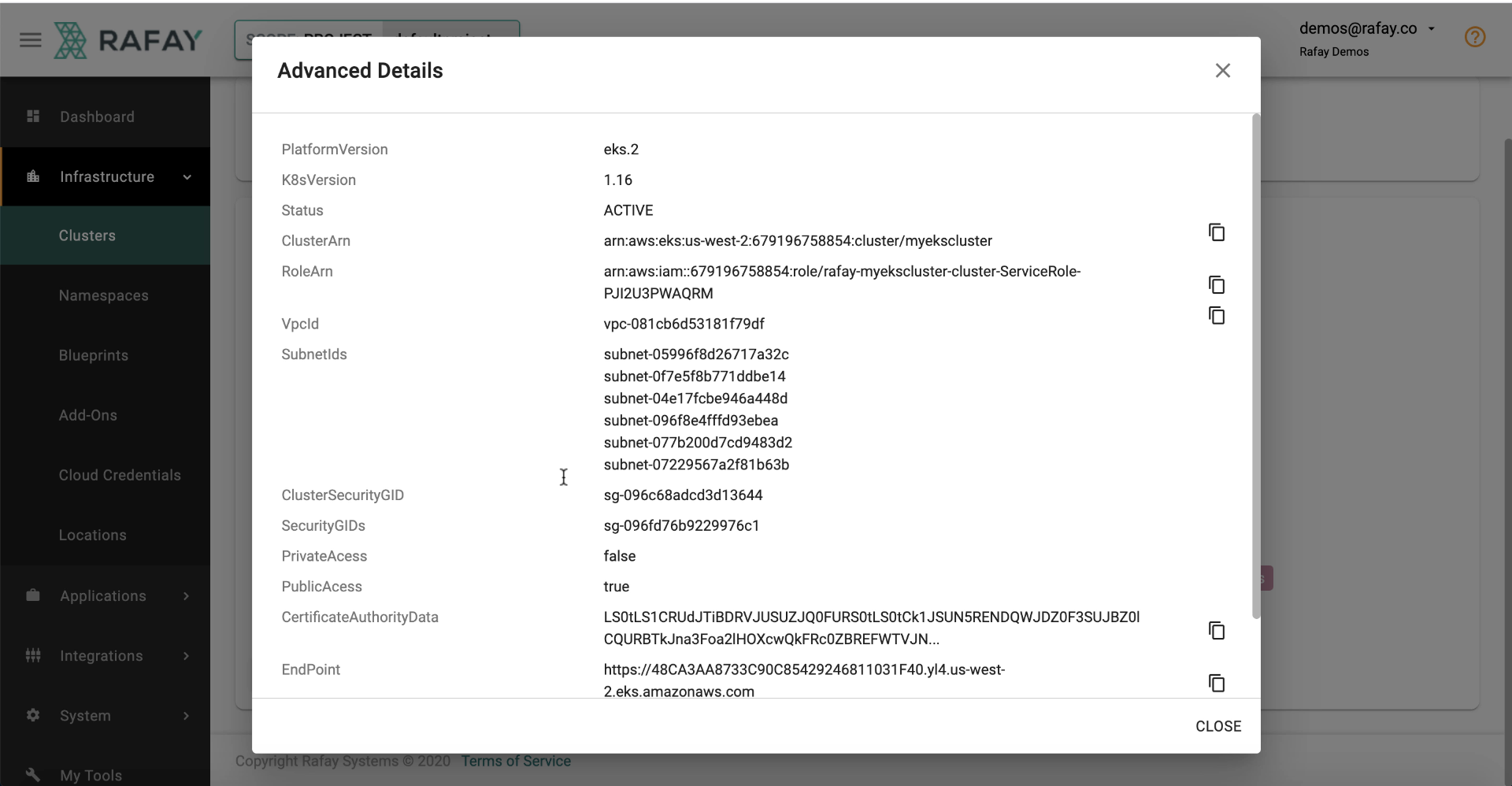
VPC CIDR 192.168.0.0/16
VPC NAT Mode Single
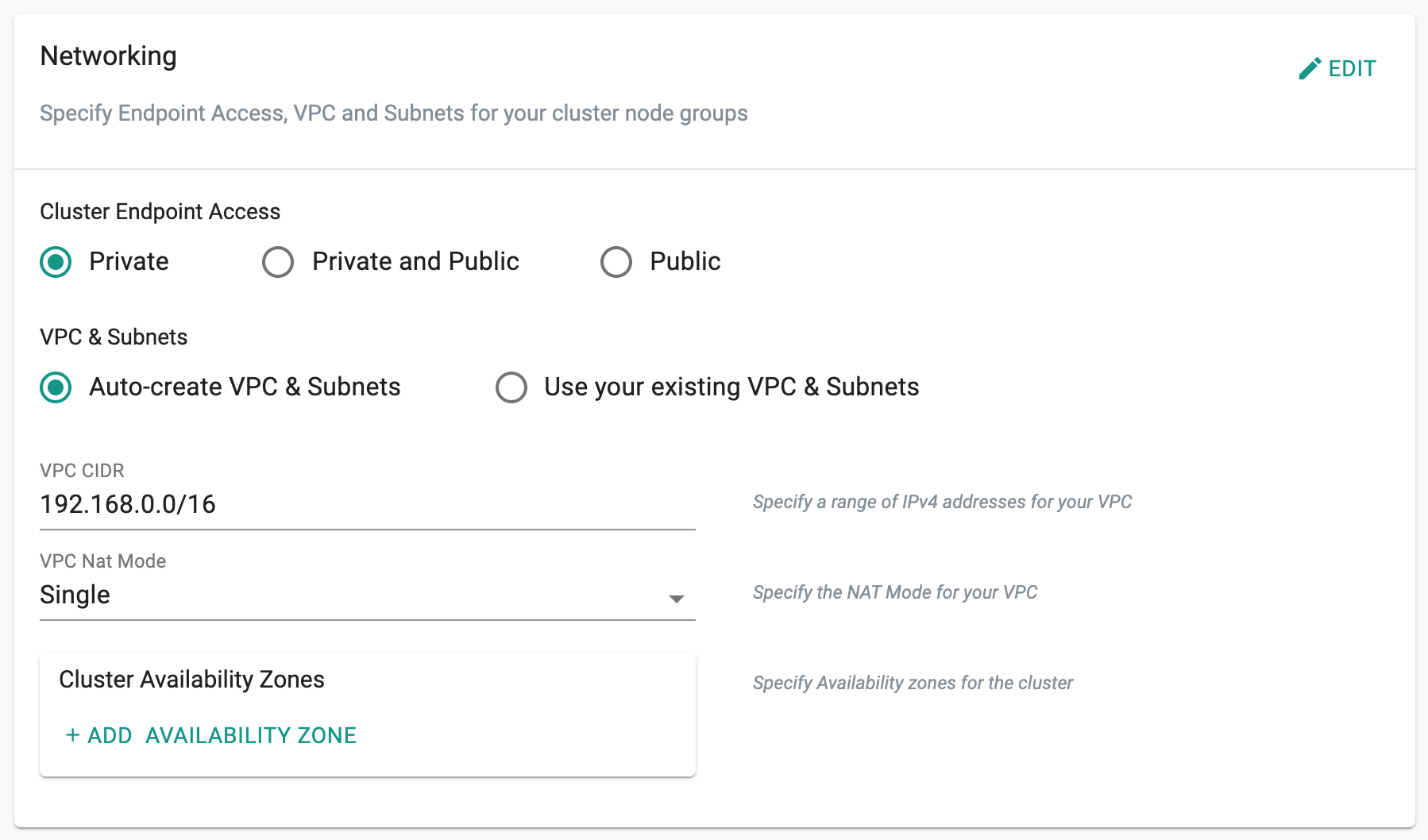
Custom¶
Users can also specify existing VPC and Public and Private subnets.
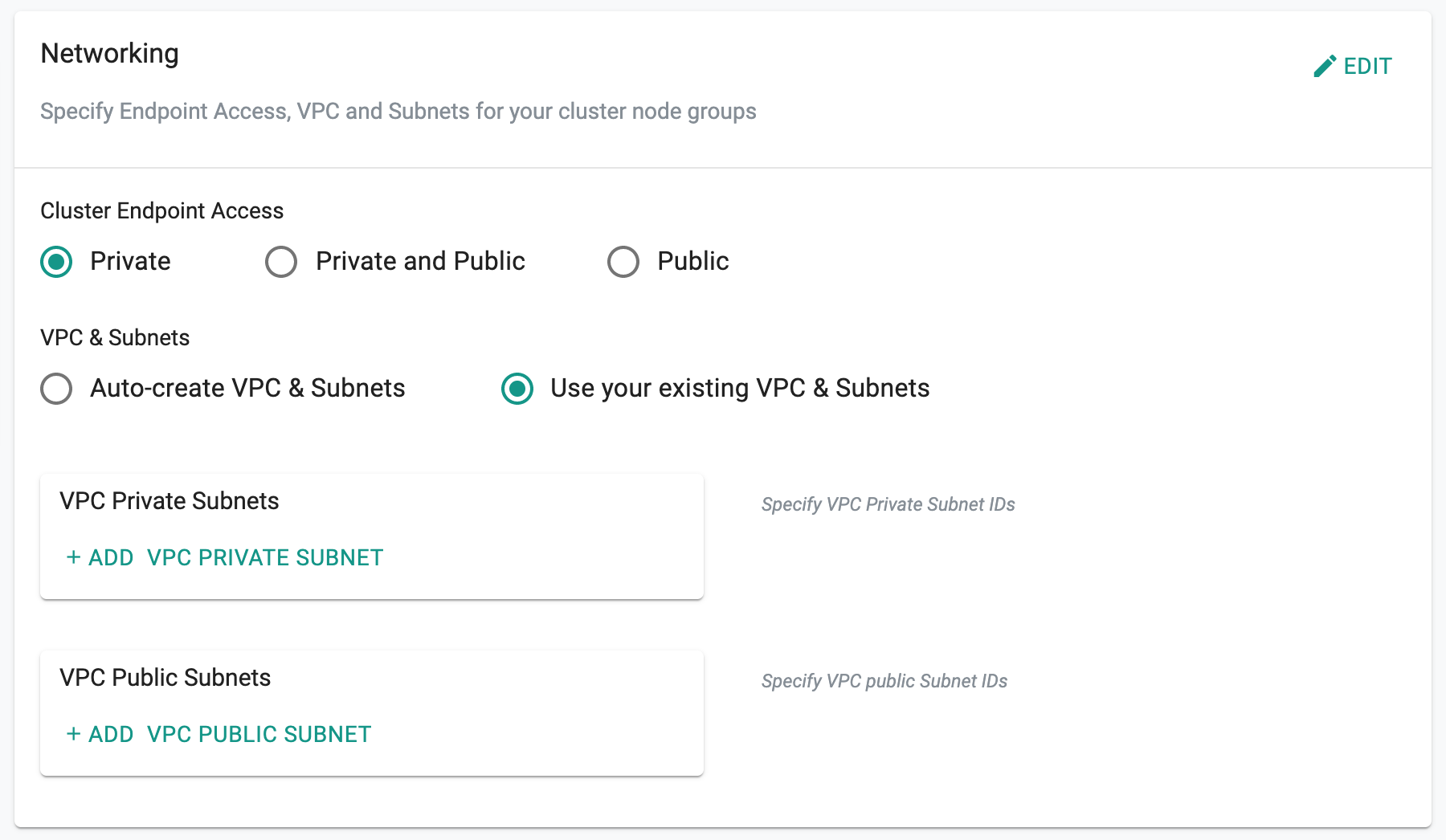
View Configuration¶
Once an Amazon EKS cluster has been provisioned by the controller, admins can view and perform a few actions on the cluster's details by selecting the "Configuration" tab.
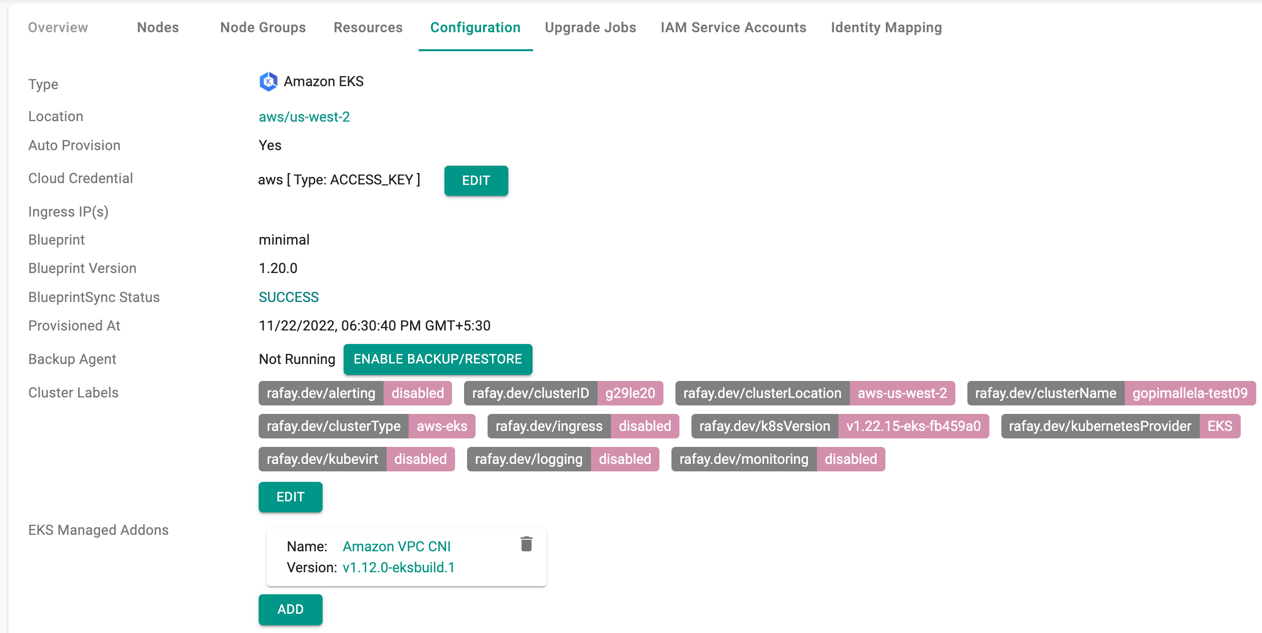
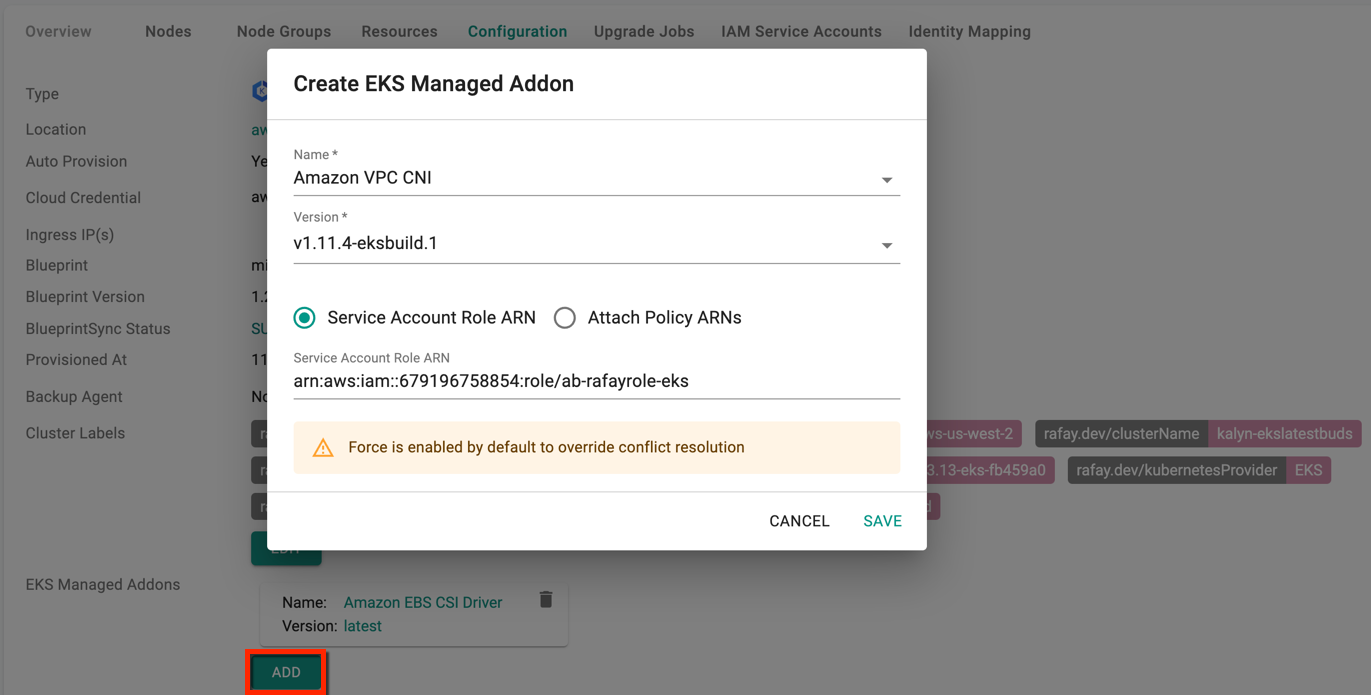
Add Managed Addons¶
To add EKS managed Addons, click Add and select the required addon from the drop-down. Currently, there are four (4) EKS managed addons. Optionally, provide Service Account Role ARN or Attach Policy ARNs and click Save
View VPC¶
To view VPC, Subnet details, etc associated with the EKS cluster, click on "View More".