Configure
In this part, you will
- Create a secret in Vault
- Configure Kubernetes Authentication
- Create a policy and a service account. You will then create a role that binds the policy with the service account so that pods have the necessary get and describe permissions to access the secret
Step 1: Create Secret¶
When Vault is run in development mode, a KV secret engine is enabled at the path /secret.
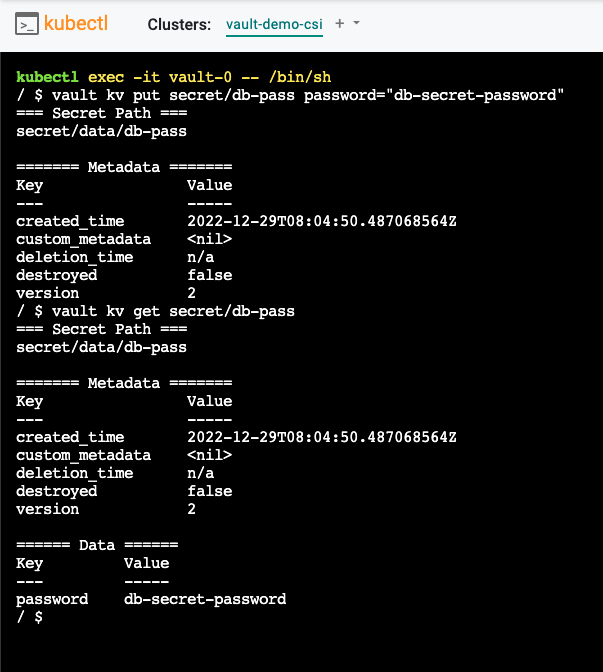
- Start an interactive shell session on the vault-0 pod
kubectl exec -it vault-0 -- /bin/sh
-
Commands issued at this prompt are executed on the vault-0 container
-
Create a secret at the path secret/db-pass with a password
vault kv put secret/db-pass password="db-secret-password"
- Verify that the secret is readable at the path secret/db-pass
vault kv get secret/db-pass
Step 2: Configure Kubernetes Authentication¶
Vault provides a Kubernetes authentication method that enables clients to authenticate with a Kubernetes Service Account Token. The Kubernetes resources that access the secret and create the volume authenticate through this method through a role.
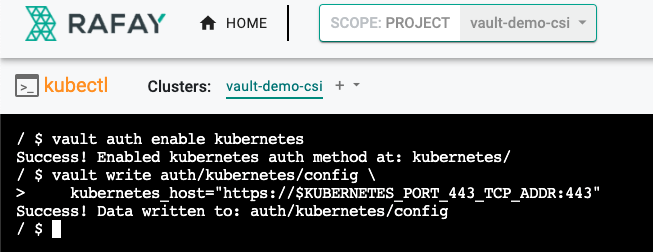
- Enable the Kubernetes authentication method
vault auth enable kubernetes
- Configure the Kubernetes authentication method with the Kubernetes API address. It will automatically use the Vault pod's own service account token. The environment variable KUBERNETES_PORT_443_TCP_ADDR references the internal network address of the Kubernetes host
vault write auth/kubernetes/config \
kubernetes_host="https://$KUBERNETES_PORT_443_TCP_ADDR:443"
Step 3: Create a policy, role and service account¶
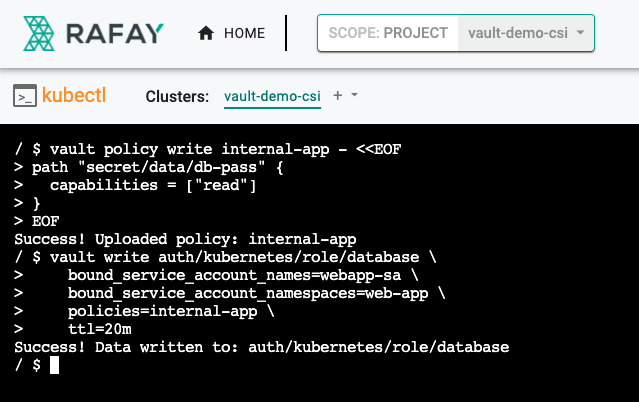
- Create a policy named "internal-app". This will be used to give the "webapp-sa" service account permission to read the kv secret created earlier
vault policy write internal-app - <<EOF
path "secret/data/db-pass" {
capabilities = ["read"]
}
EOF
- Create a Kubernetes authentication role named "database" that binds this policy with a Kubernetes service account named webapp-sa
vault write auth/kubernetes/role/database \
bound_service_account_names=webapp-sa \
bound_service_account_namespaces=web-app \
policies=internal-app \
ttl=20m
The role connects the Kubernetes service account "webapp-sa" in the namespace "web-app" with the Vault policy "internal-app".
Exit the vault-0 pod.
exit
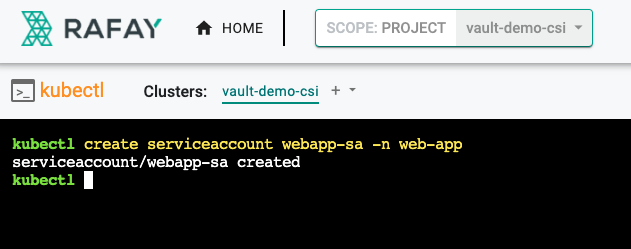
- Create a namespace where the test pod will be deployed (e.g. web-app), create a service account named "webapp-sa" in that namespace
kubectl create serviceaccount webapp-sa -n web-app
Next Steps¶
You are now ready to move on to the next part of the recipe where you will create a workload and access the secrets.