Test
What Will You Do¶
In this exercise you will create and deploy two test workloads in different namespaces to verify the network policy has been properly deployed to namespace-a
Assumptions¶
- You have already configured and installed Network Policy on your upstream Kubernetes cluster
Step 1: Create Namespace-a Manifest¶
- Copy the file below and save as deployment-namespace-a.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: praqma
name: debug
namespace: namespace-a
spec:
replicas: 3
selector:
matchLabels:
app: praqma
template:
metadata:
labels:
app: praqma
spec:
containers:
- image: praqma/network-multitool:latest
imagePullPolicy: Always
name: debug
restartPolicy: Always
Step 2: Create Namespace-b Manifest¶
- Copy the file below and save as deployment-namespace-b.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: praqma
name: debug
namespace: namespace-b
spec:
replicas: 3
selector:
matchLabels:
app: praqma
template:
metadata:
labels:
app: praqma
spec:
containers:
- image: praqma/network-multitool:latest
imagePullPolicy: Always
name: debug
restartPolicy: Always
Step 3: Create NameSpace A Workload¶
- Under Applications, select "Workloads"
- Select "New Workload" and enter a Name, set Package Type to "k8s YAML", and select the Namespace namespace-a
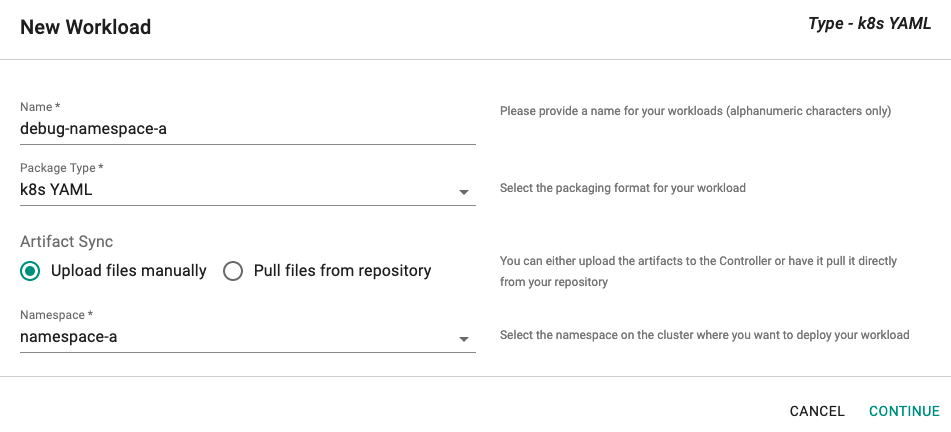
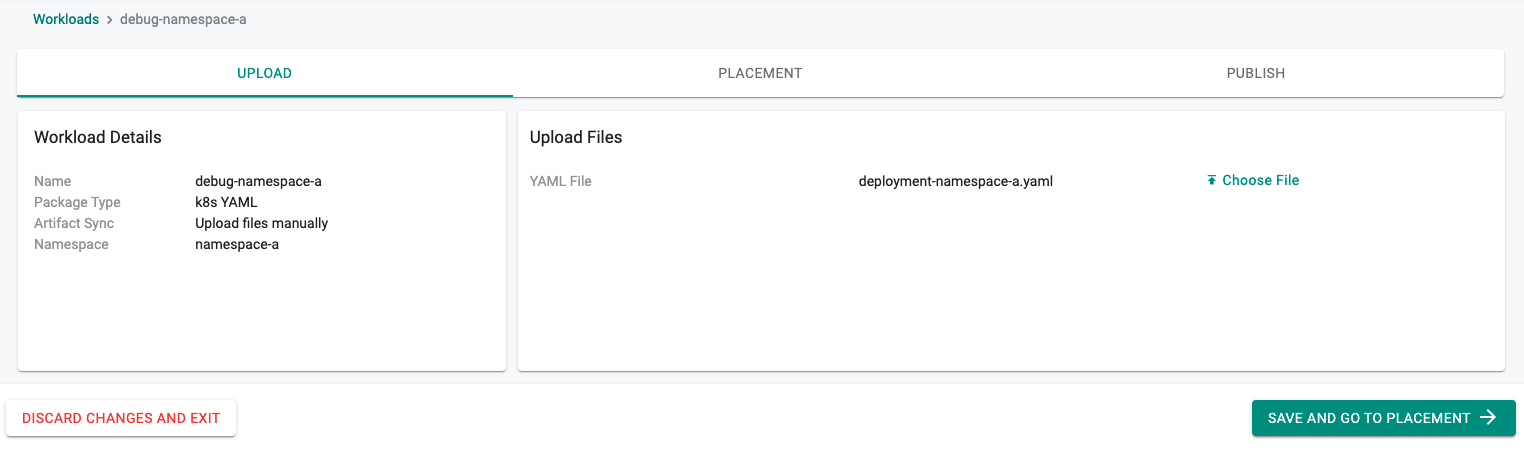
- Upload file deployment-namespace-a.yaml
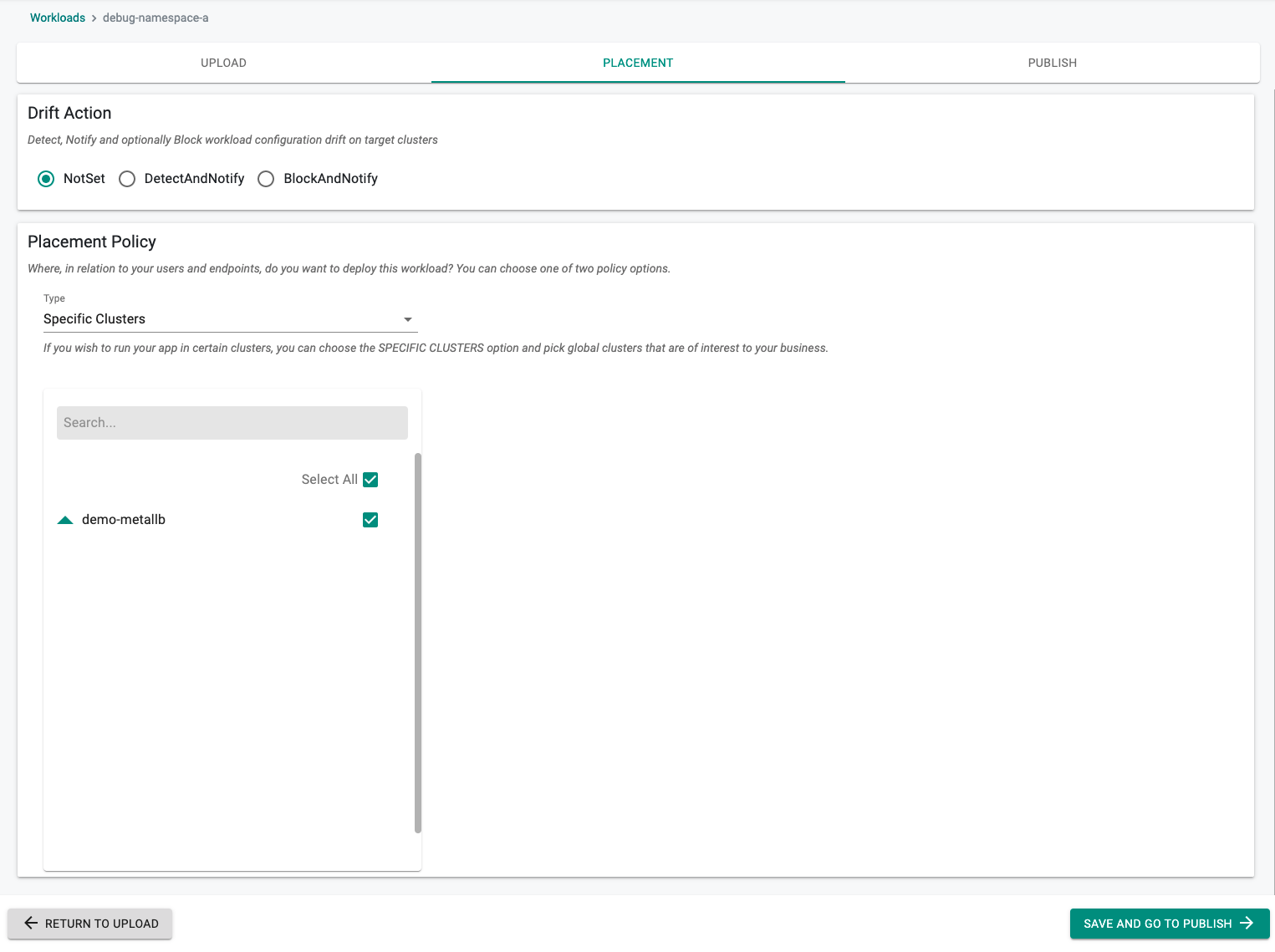
- Set the placement
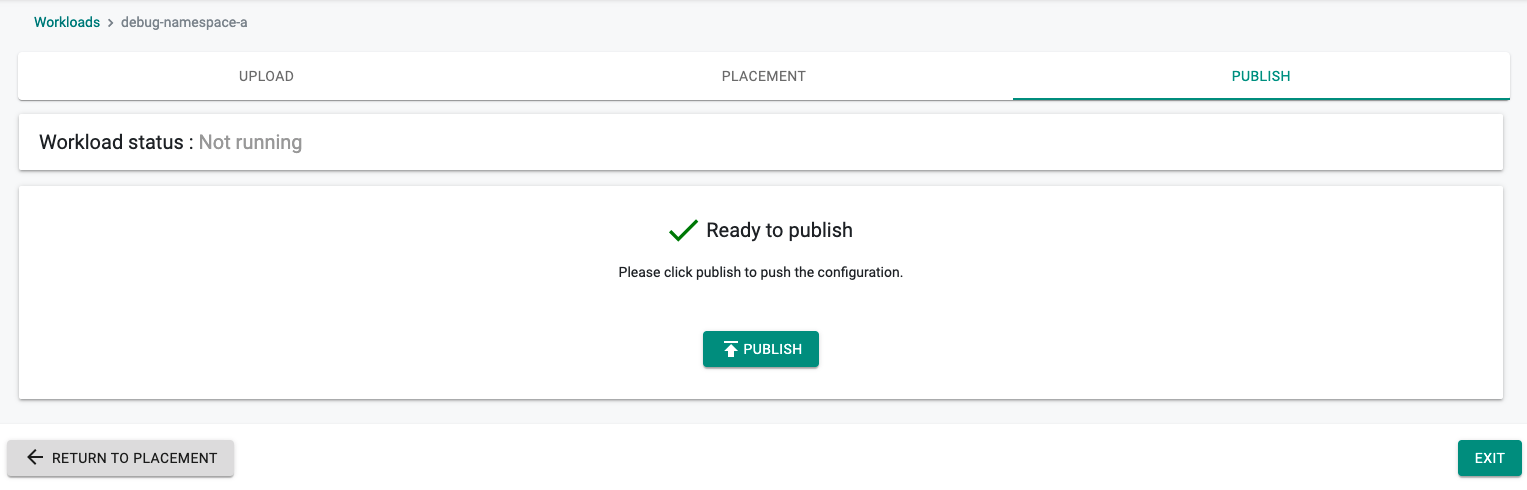
- Publish Workload
Step 4: Create NameSpace B Workloads¶
Under Applications, select "Workloads" - Select "New Workload" and enter a Name, set Package Type to "k8s YAML", and select the Namespace namespace-b
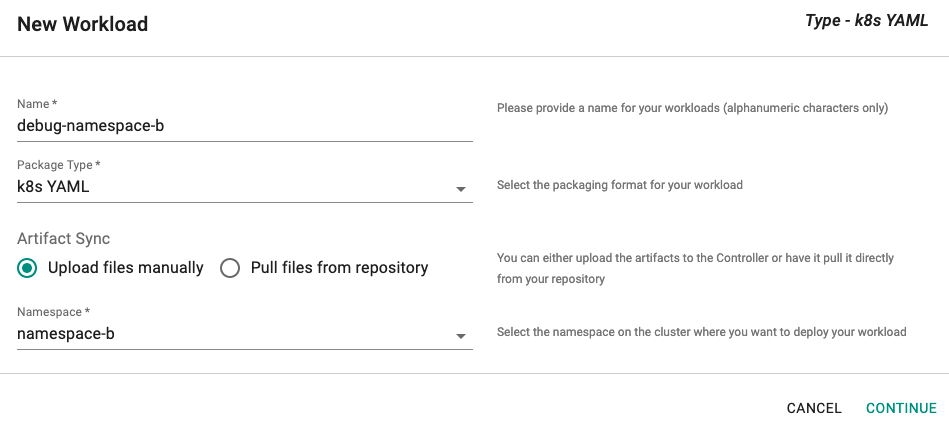
- Upload file deployment-namespace-b.yaml
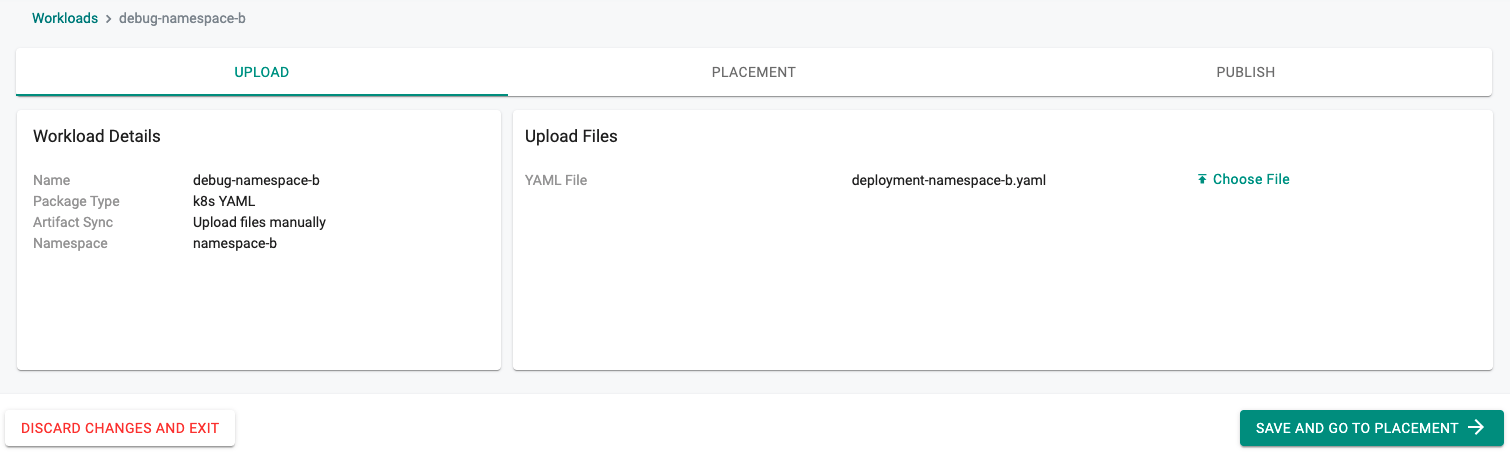
- Set the placement
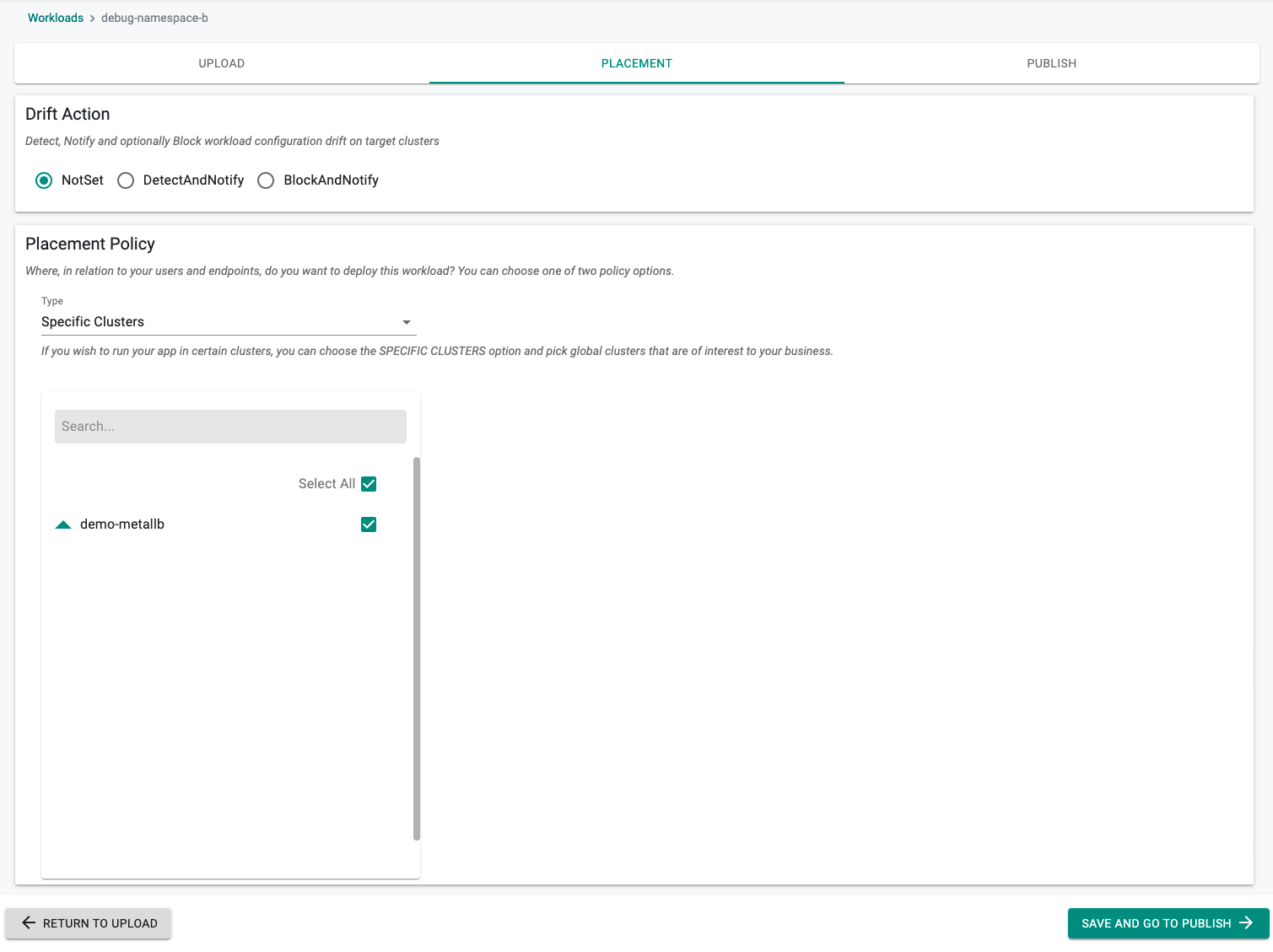
- Publish Workload
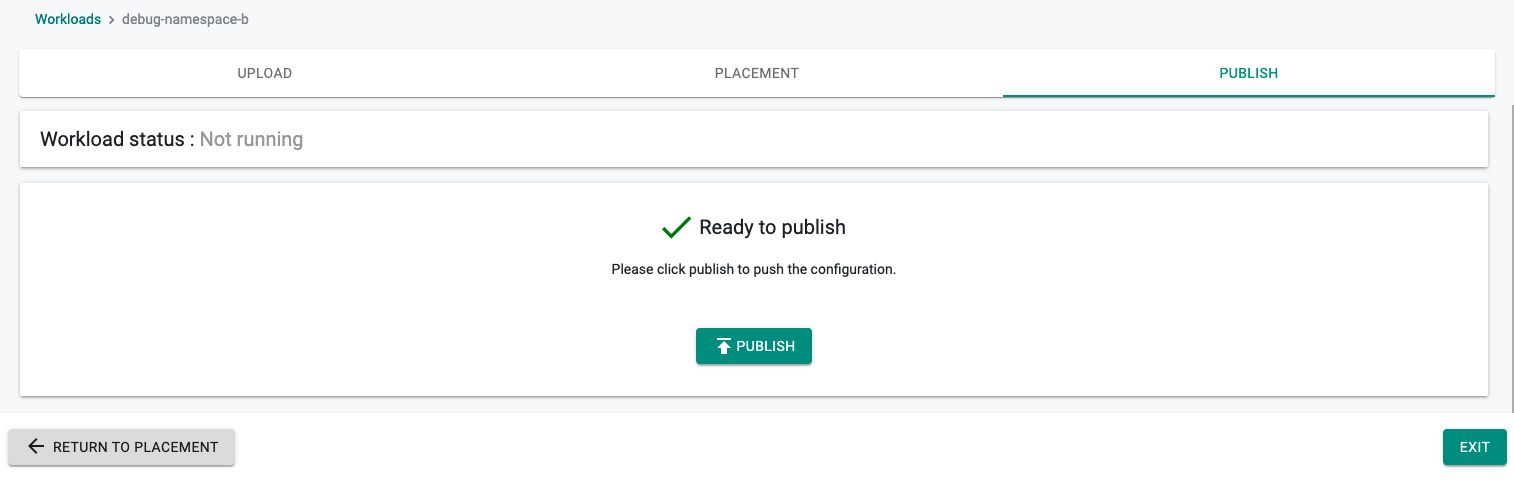
Step 5: Verify Workload¶
Click on the Kubectl button on the cluster to open a virtual terminal and run the following kubectl command
kubectl get pod -n namespace-a -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
debug-79d8b57ff4-5svbq 1/1 Running 0 16m 10.244.0.47 mac-demo <none> <none>
debug-79d8b57ff4-7d7g5 1/1 Running 0 16m 10.244.0.48 mac-demo <none> <none>
debug-79d8b57ff4-g2ptf 1/1 Running 0 16m 10.244.0.49 mac-demo <none> <none>
kubectl get pod -n namespace-b -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
debug-744ff55bbf-cw2sx 1/1 Running 0 8m7s 10.244.0.50 mac-demo <none> <none>
debug-744ff55bbf-m8g6z 1/1 Running 0 8m7s 10.244.0.52 mac-demo <none> <none>
debug-744ff55bbf-rd56n 1/1 Running 0 8m7s 10.244.0.51 mac-demo <none> <none>
kubectl get pod -n rafay-infra -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
log-aggregator-68db4c7c77-5gjgk 1/1 Running 1 32h 10.244.0.31 mac-demo <none> <none>
log-router-5n2wg 2/2 Running 16 7d1h 10.244.0.40 mac-demo <none> <none>
rafay-metrics-server-679c698f9f-zr6p2 1/1 Running 6 7d1h 10.244.0.43 mac-demo <none> <none>
rafay-prometheus-adapter-6fd9868c56-mf6wf 1/1 Running 6 7d1h 10.244.0.34 mac-demo <none> <none>
rafay-prometheus-alertmanager-0 2/2 Running 12 7d1h 10.244.0.44 mac-demo <none> <none>
rafay-prometheus-helm-exporter-6b8cb59775-vpffw 1/1 Running 1 32h 10.244.0.27 mac-demo <none> <none>
rafay-prometheus-kube-state-metrics-cd48f5595-9n6g4 1/1 Running 6 7d1h 10.244.0.28 mac-demo <none> <none>
rafay-prometheus-node-exporter-2542c 1/1 Running 6 7d1h 10.244.0.41 mac-demo <none> <none>
rafay-prometheus-server-0 2/2 Running 12 7d1h 10.244.0.26 mac-demo <none> <none>
Step 6: Verify Network policy¶
- Go to workloads and right-click on Actions and select Debug
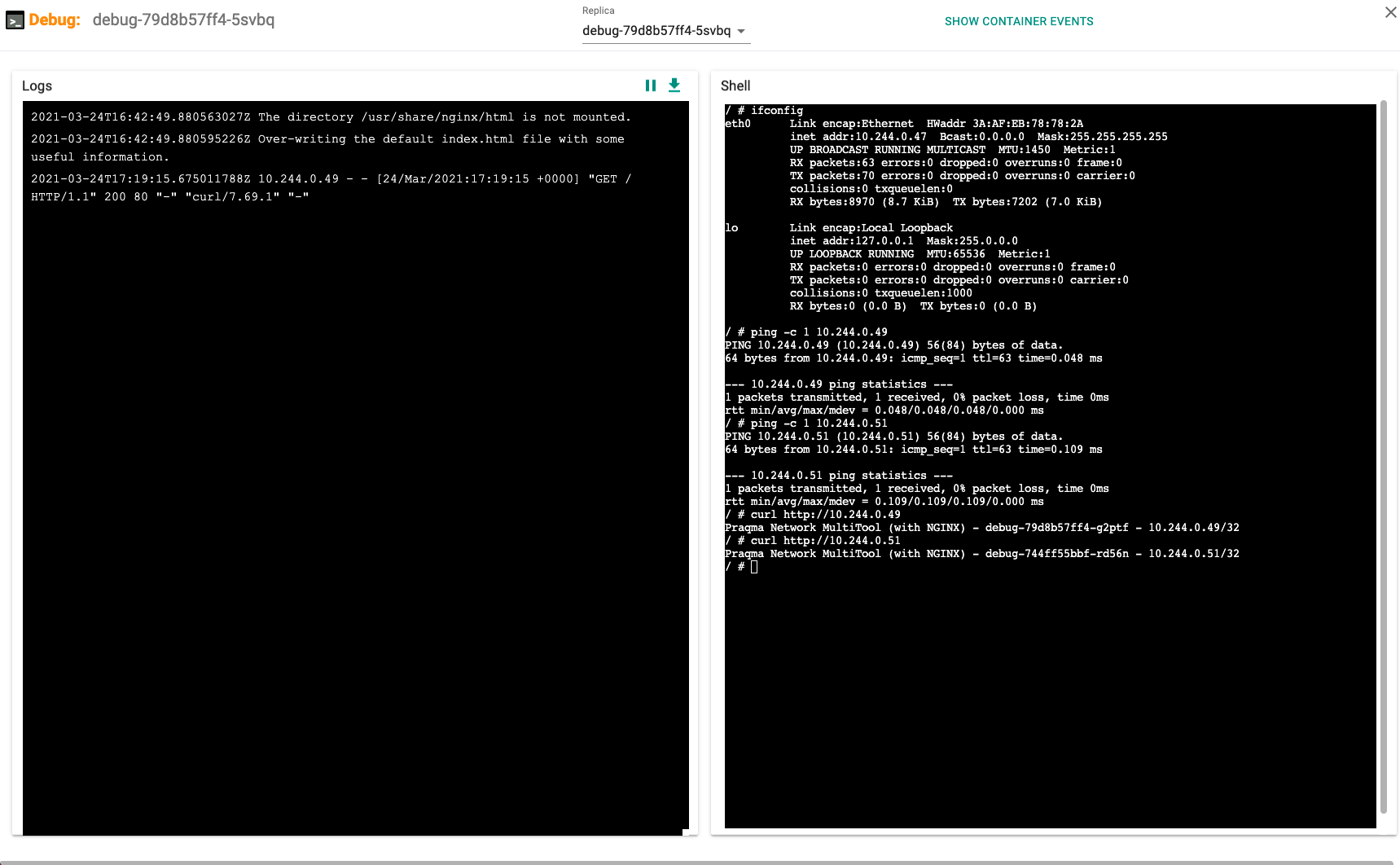
- Select the LAUNCH option for any one of the pods in namespace-a. It will open up a shell into the container. You should be able to ping and run a curl command and access pods in namespace-a and namespace-b. All other namespaces will be denied.
# ping -c 1 10.244.0.49
PING 10.244.0.49 (10.244.0.49) 56(84) bytes of data.
64 bytes from 10.244.0.49: icmp_seq=1 ttl=63 time=0.050 ms
--- 10.244.0.49 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.050/0.050/0.050/0.000 ms
# ping -c 1 10.244.0.51
PING 10.244.0.51 (10.244.0.51) 56(84) bytes of data.
64 bytes from 10.244.0.51: icmp_seq=1 ttl=63 time=0.047 ms
--- 10.244.0.51 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.047/0.047/0.047/0.000 ms
# curl http://10.244.0.49
Praqma Network MultiTool (with NGINX) - debug-79d8b57ff4-g2ptf - 10.244.0.49/32
# curl http://10.244.0.51
Praqma Network MultiTool (with NGINX) - debug-744ff55bbf-rd56n - 10.244.0.51/32
# ping -c 1 10.244.0.26
PING 10.244.0.26 (10.244.0.26) 56(84) bytes of data.
--- 10.244.0.26 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
Recap¶
Congratulations! You have successfully created and deployed a network policy.