CNI Providers
CNI Providers¶
CNI providers help to create a framework for configuring the appropriate network configuration and resources when provisioning/de-provisioning containers. The CNI spec outlines a plugin interface for container runtimes to coordinate with plugins to configure networking. The two CNI providers are AWS and Calico
AWS
AWS uses Amazon VPC Container Network Interface (CNI) plugin for the pod networking in EKS clusters provisioned by the controller. AWS CNI is the default CNI Provider. AWS VPC ensures that CNI plugin daemons are scheduled on all nodes in a cluster and adds elastic network interface (ENI) resource tagging
Calico
Calico is a popular networking solution used to interconnect virtual machines or Linux containers with the help of virtual routers. Calico provides a Cluster Network Interface (CNI) plugin that can be used for integration with Kubernetes. Users who prefer flexible IP address management capabilities can select the Calico CNI provider. On selecting Calico, all the pods related to Calico gets installed
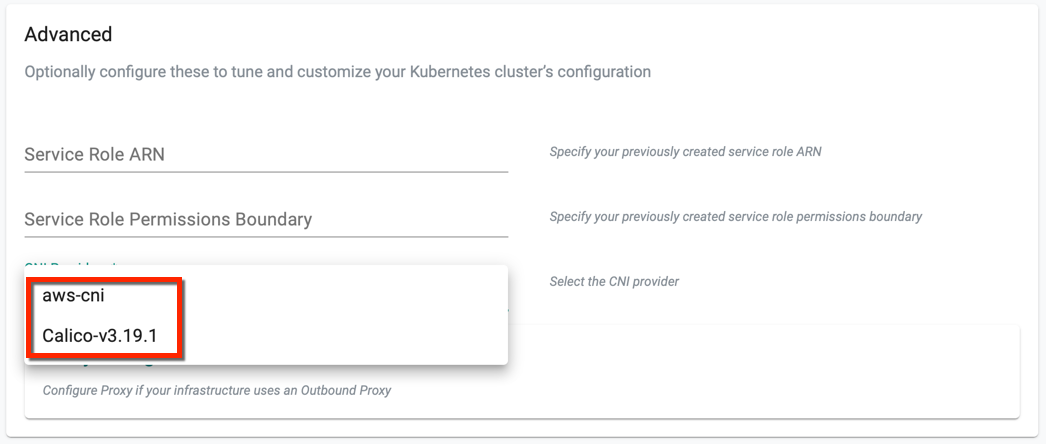
CNI Providers in Controller¶
During EKS Cluster provisioning, user must select a CNI Provider from the CNI Providers drop-down available in Advance Settings. If none of the CNI is selected, AWS is set as the default CNI provider
CNI Providers through CLI¶
Users can use the cluster config yaml file to provision the cluster with Calico CNI. Below is an illustrative example of a cluster config file with the CNI Provider Calico
kind: Cluster
metadata:
name: demo-ekscluster
project: project1
spec:
blueprint: bp-with-co-addon
blueprintversion: v1
cloudprovider: demo-provider
clusterConfig: null
cniprovider: Calico-v3.19.1
proxyconfig: {}
type: eks
---
apiVersion: rafay.io/v1alpha5
kind: ClusterConfig
metadata:
name: demo-ekscluster
region: us-west-1
version: "1.19"
nodeGroups:
- amiFamily: AmazonLinux2
desiredCapacity: 2
iam:
withAddonPolicies:
autoScaler: true
imageBuilder: true
instanceType: t3.xlarge
maxSize: 2
minSize: 2
name: ng-2220fc4d
volumeSize: 80
volumeType: gp3
vpc:
cidr: 192.168.0.0/16
clusterEndpoints:
privateAccess: true
publicAccess: true
nat:
gateway: Single
Use the below command in the terminal to apply the changes
./rctl apply -f <filename>
Important
- All the pods that implement admission webhooks should have hostnetwork to true when using Calico CNI provider