Access
In this part, you will
- Create a K8s YAML workload that will create a SecretStore
- Create a K8s YAML workload that will create an ExternalSecret
- Verify the secret is available in the namespace
Step 1: Create SecretStore¶
To take advantage of the External Secrets Operator a SecretStore custom resource will need to be created. This defines the service we are using, the region, and the service account we are using.
Important
The SecretStore must be in the same namespace as the ExternalSecret
Create and Publish Workload¶
- Create a file called "secret-store-app-team-1.yaml" from the spec below
apiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: eso-secret-store
spec:
provider:
aws:
service: SecretsManager
region: us-west-2
auth:
jwt:
serviceAccountRef:
name: my-secret-irsa
-
Click on Application -> Workloads
-
Click on Create New Workload with the name "secret-store-app-team-1"
-
Select "K8s YAML" for addon type
-
Select "Upload files manually" for Artifact Sync
-
Select the "app-team-1" namespace from the dropdown
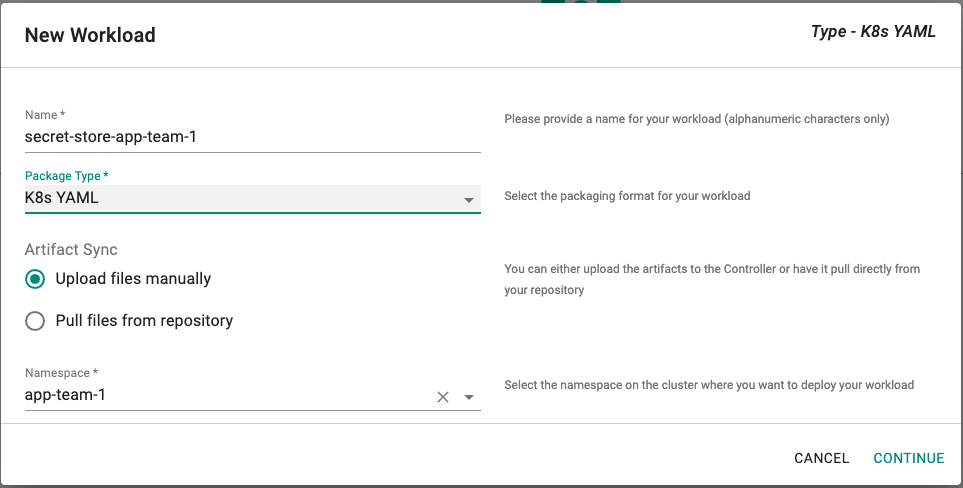
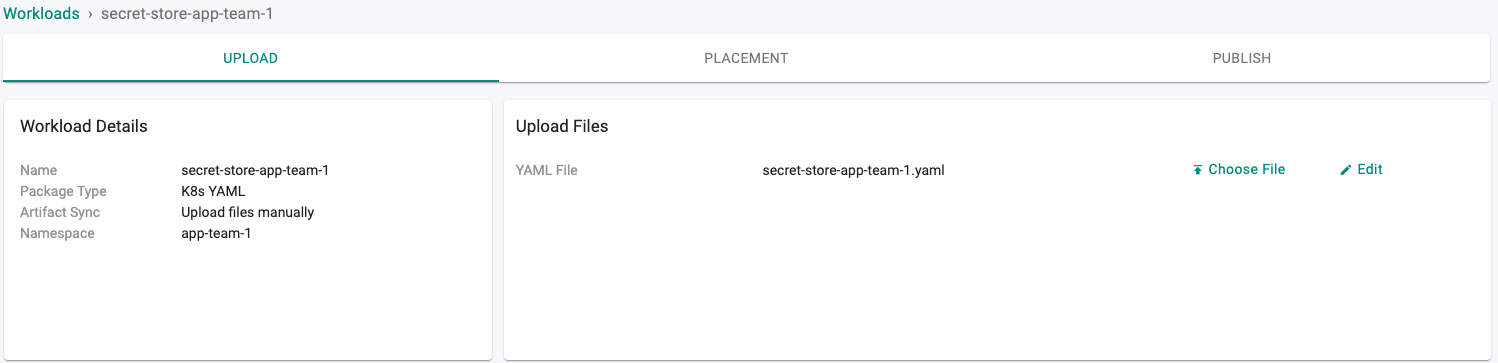
- Select the file "secret-store-app-team-1.yaml" created above
- Select a cluster for the placement policy
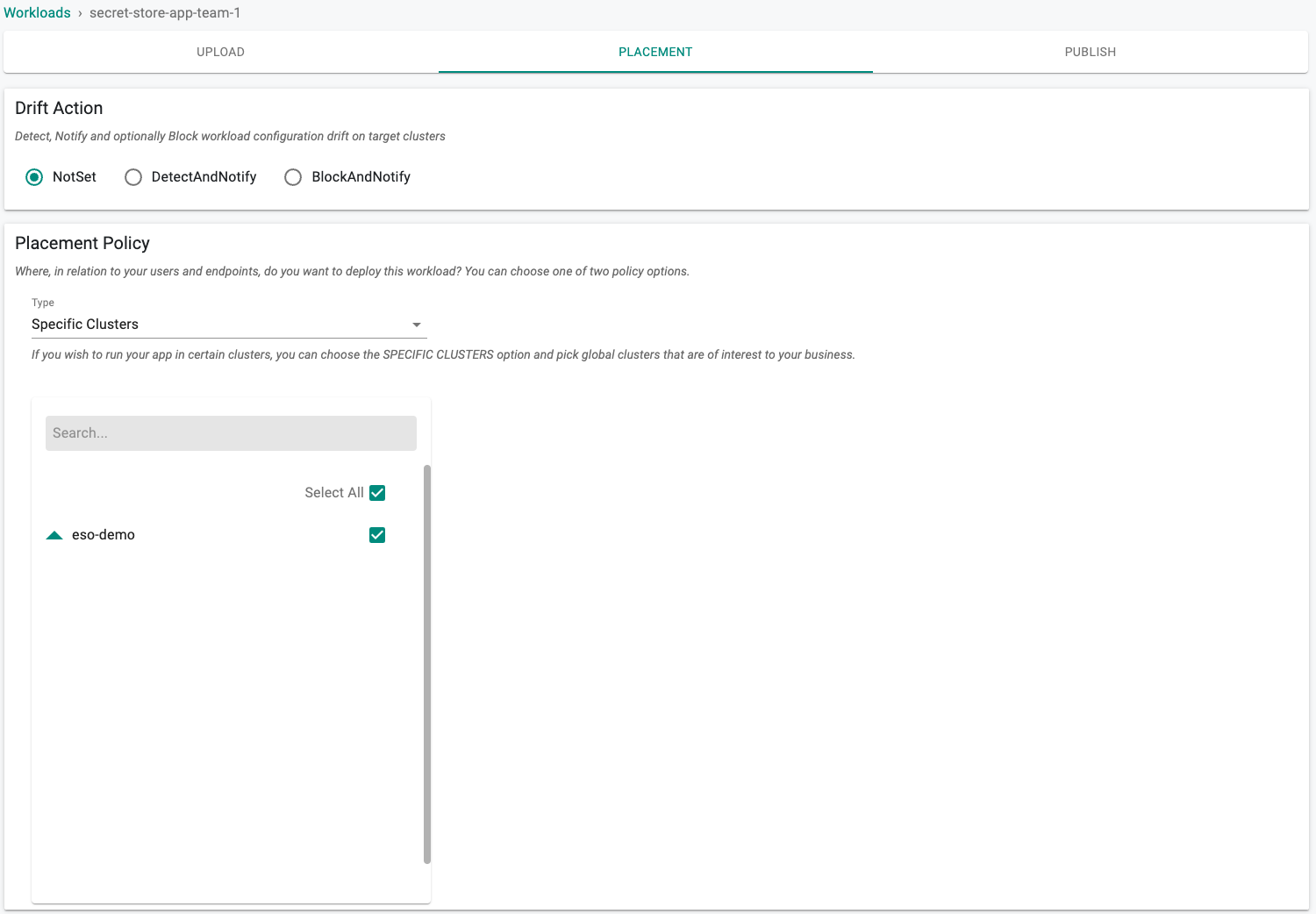
- Click on "SAVE AND GO TO PUBLISH"
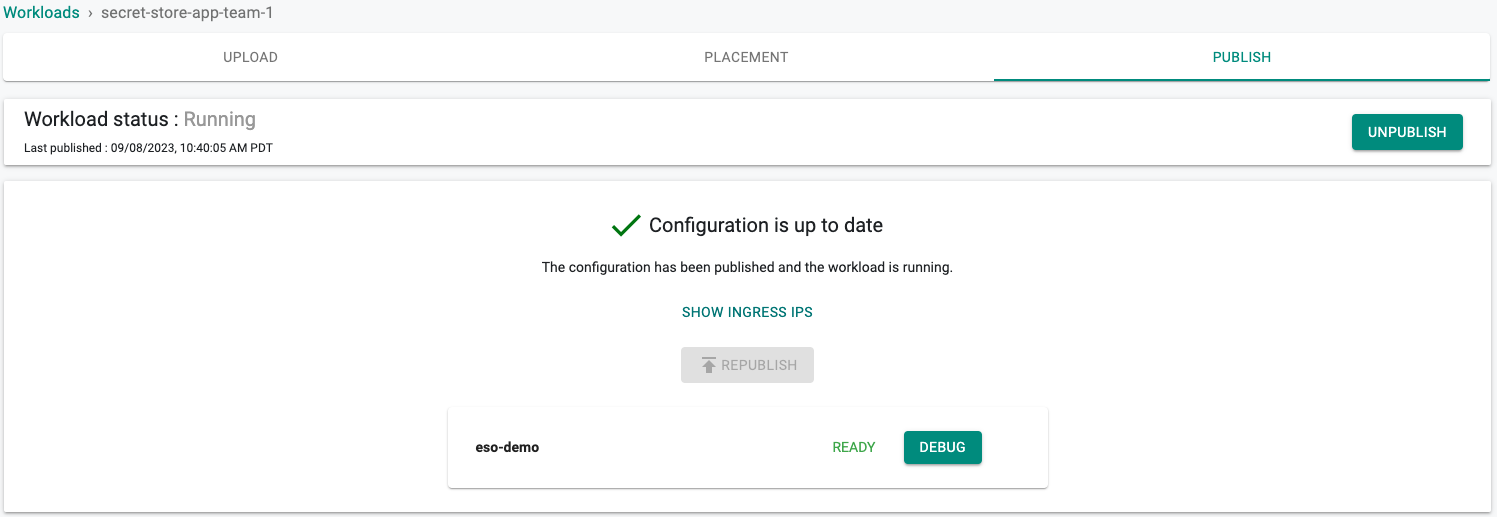
- Click on "PUBLISH"
In a minute the workload should be deployed.
Step 2: Create ExternalSecret¶
To take advantage of the External Secrets Operator an ExternalSecret custom resource will need to be created. This defines the service we are using, the region, and the service account we are using.
Important
The ExternalSecret must be in the same namespace as the SecretStore
Create and Publish Workload¶
- Create a file called "external-secret-app-team-1.yaml" from the spec below
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: eso-demo
spec:
secretStoreRef:
name: eso-secret-store
kind: SecretStore
target:
name: eso-secret
creationPolicy: Owner
data:
- secretKey: eso-username
remoteRef:
key: test/eso/testSecret #AWS secret name
property: username #AWS secret username
- secretKey: eso-password
remoteRef:
key: test/eso/testSecret #AWS secret name
property: password #AWS secret password
-
Click on Application -> Workloads
-
Click on Create New Workload with the name "external-secret-app-team-1"
-
Select "K8s YAML" for addon type
-
Select "Upload files manually" for Artifact Sync
-
Select the "app-team-1" namespace from the dropdown
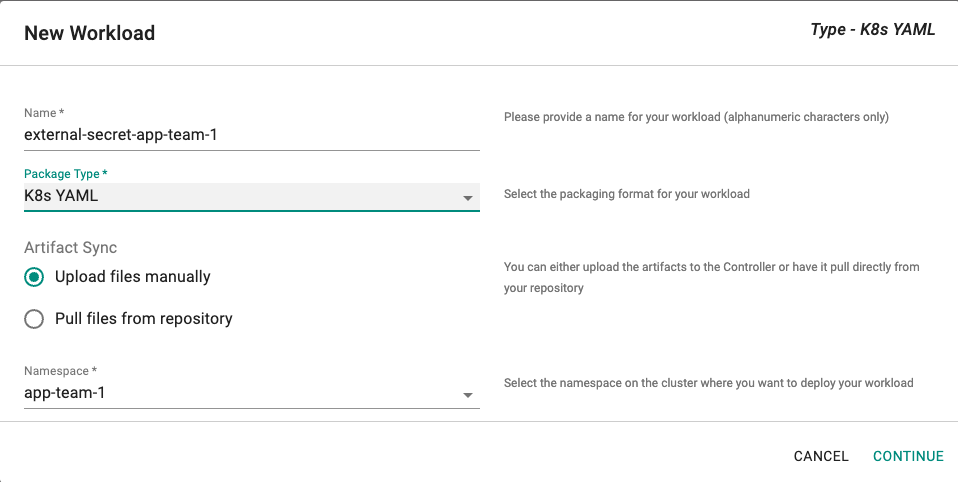
- Select the file "external-secret-app-team-1.yaml" created above
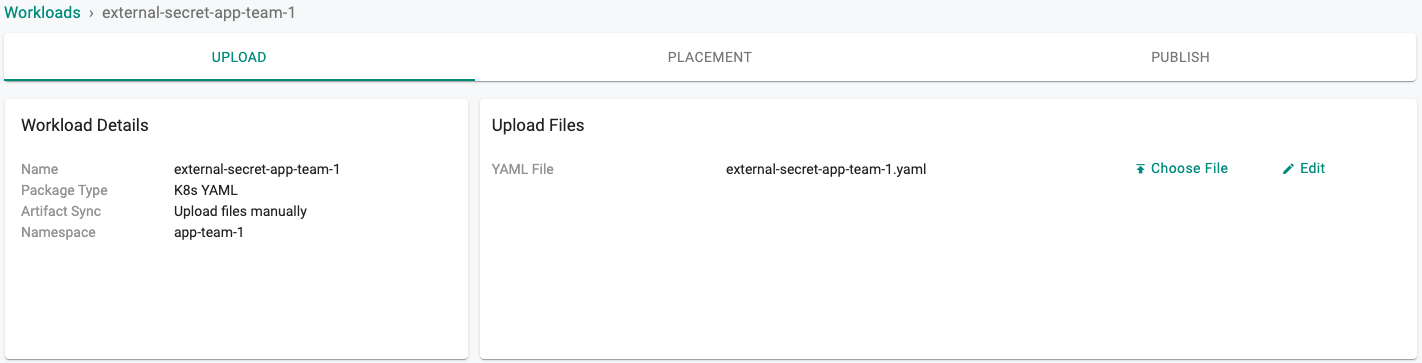
- Select a cluster for the placement policy
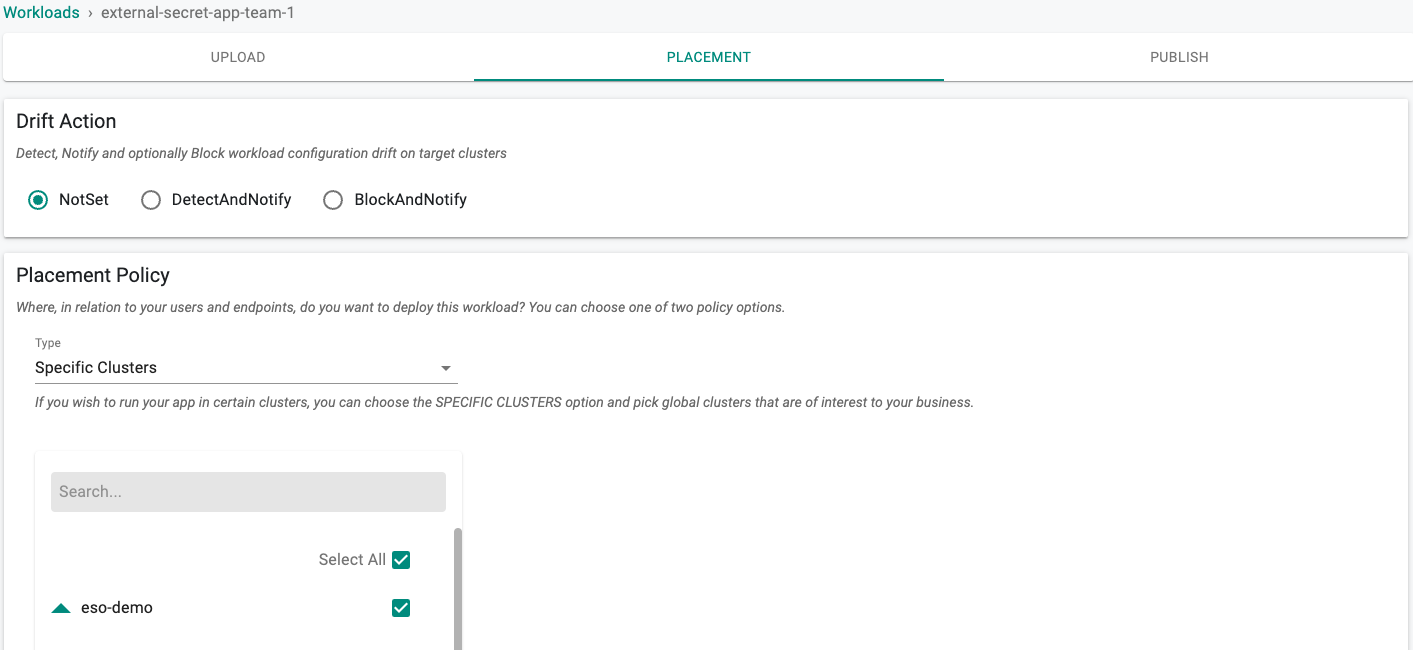
- Click on "SAVE AND GO TO PUBLISH"
- Click on "PUBLISH"
In a minute the workload should be deployed.
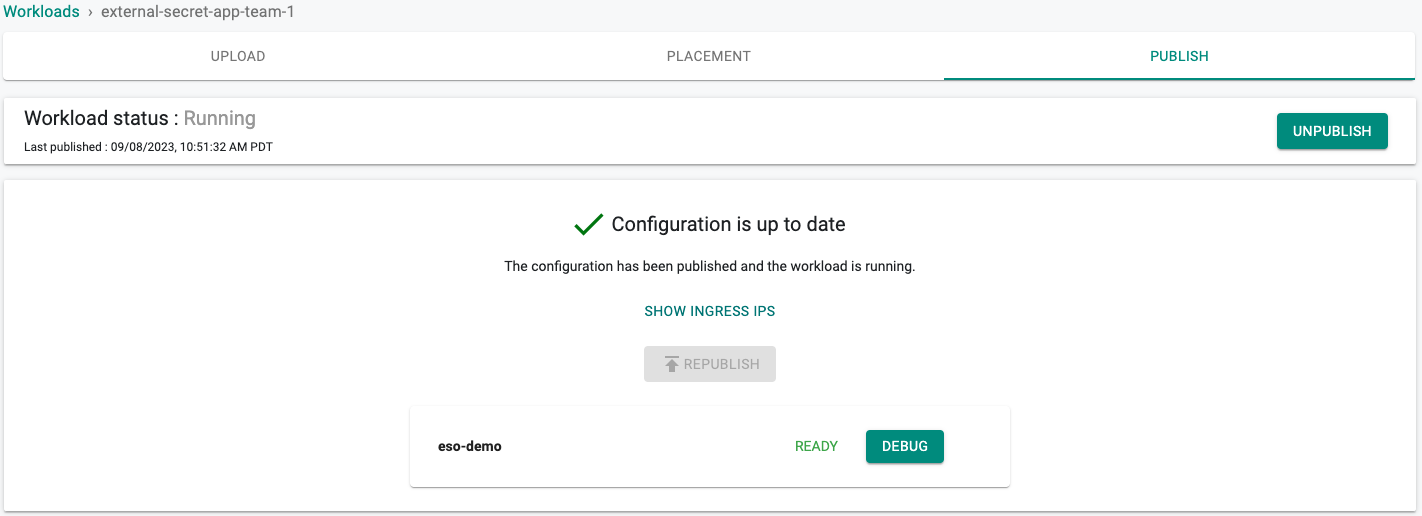
Step 3: Verify Setup¶
After deploying the SecretStore and ExternalSecret manifests this should have pulled the secret from AWS Secrets Manager and synchronized it to a K8s secret. We can validate the K8s secret has been properly created on our cluster.
- Click on the EKS cluster
- Select Resources to view the integrated k8s dashboard
- Expand "Config & Storage"
- Select "Secrets" from the resource selector and filter by the "app-team-1" namespace
- The newly created secret "eso-secret" should be present
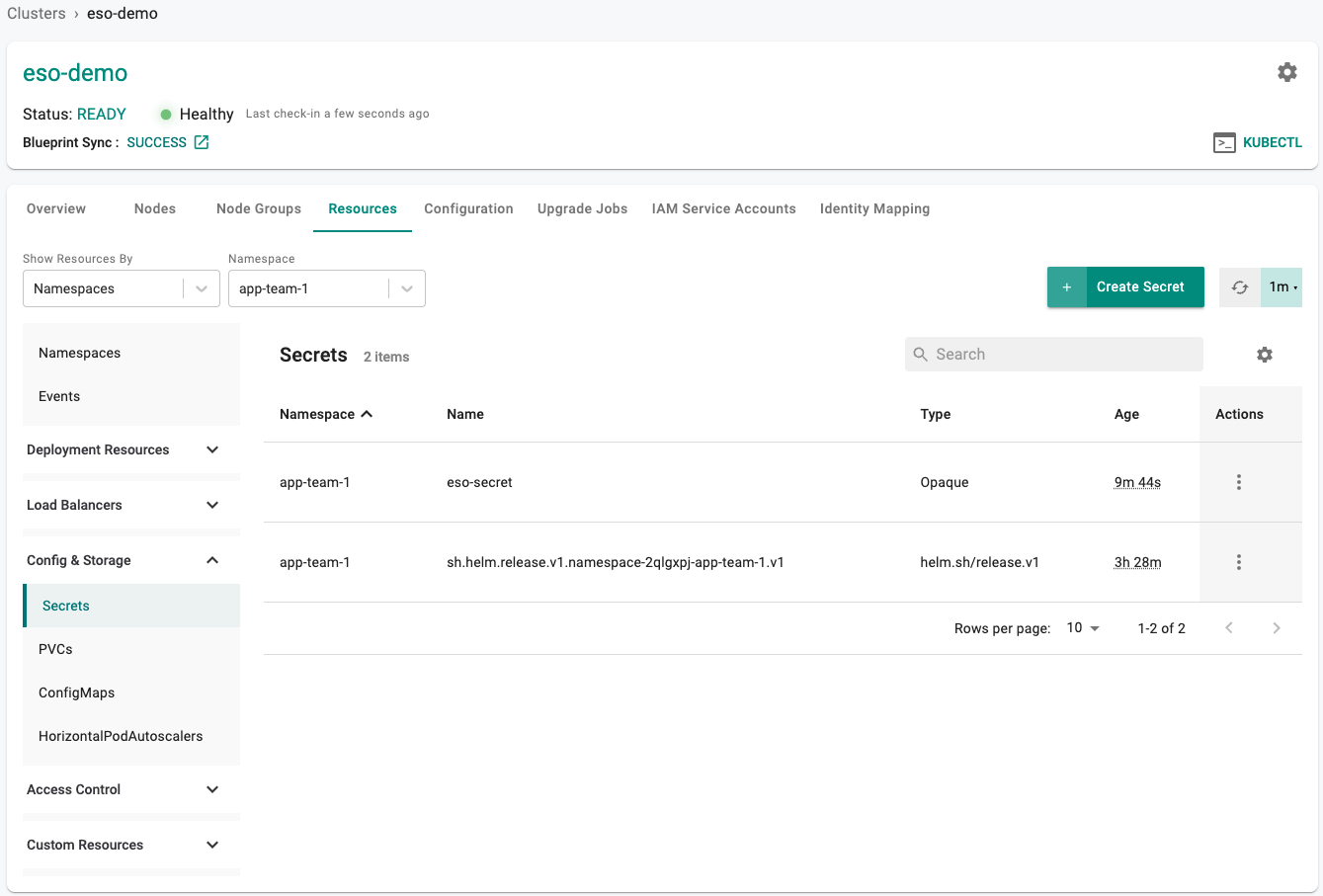
- Describe the secret
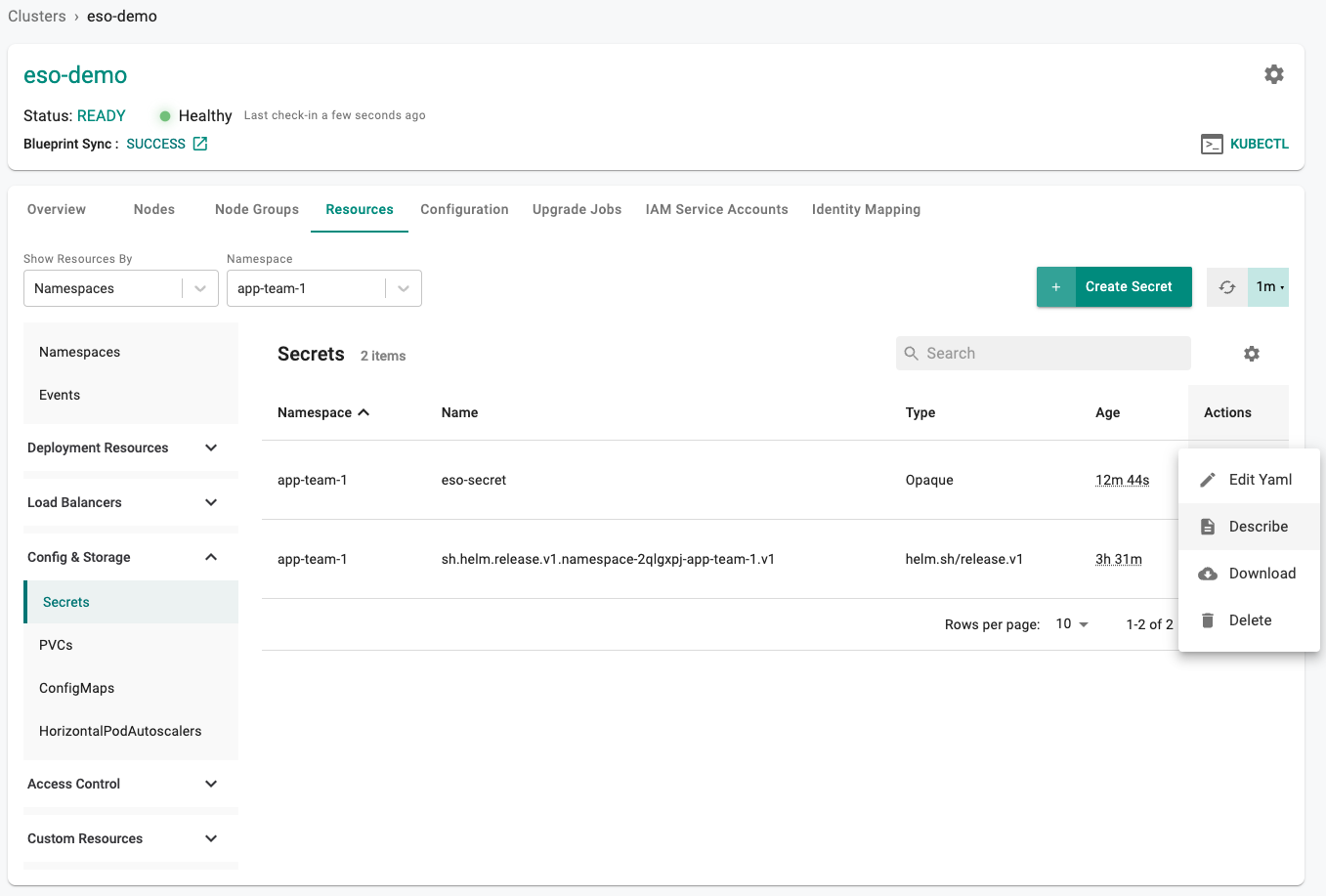
- Verify the Data contains the following keys "eso-password" and "eso-username"
Name: eso-secret
Namespace: app-team-1
Labels: k8smgmt.io/project=defaultproject
rep-cluster=krxw1wk
rep-cluster-name=eso-demo
rep-drift-reconcillation=disabled
rep-organization=d2w714k
rep-partner=rx28oml
rep-placement=2q9olw9
rep-project=1ky7ygk
rep-project-name=defaultproject
rep-workload=external-secret-app-team-1
rep-workloadid=kog94vj
Annotations: reconcile.external-secrets.io/data-hash: ce51777b12110d1a8c495bd4d9bedcec
Type: Opaque
Data
====
eso-password: 10 bytes
eso-username: 5 bytes
Recap¶
Congratulations! You have successfully created a cluster blueprint with the External Secrets Operator addon and used it to sync a secret stored in AWS Secrets Manager to a K8s secret on your cluster. You can now use this blueprint on as many clusters as you require to synchronize secrets stored in AWS Secrets Manager.