Using Amazon EKS Pod Identity and Associations with Rafay - Part 2¶
In continuation of our Part 1 of our blog introducing Pod Identity vs. IRSA for Amazon EKS, this is Part 2, where we will explore how to use Amazon EKS Pod Identity with the Rafay platform. This blog post will guide you through deploying the Amazon EKS Pod Identity Agent and configuring role associations, enabling your Kubernetes pods to securely access AWS services.
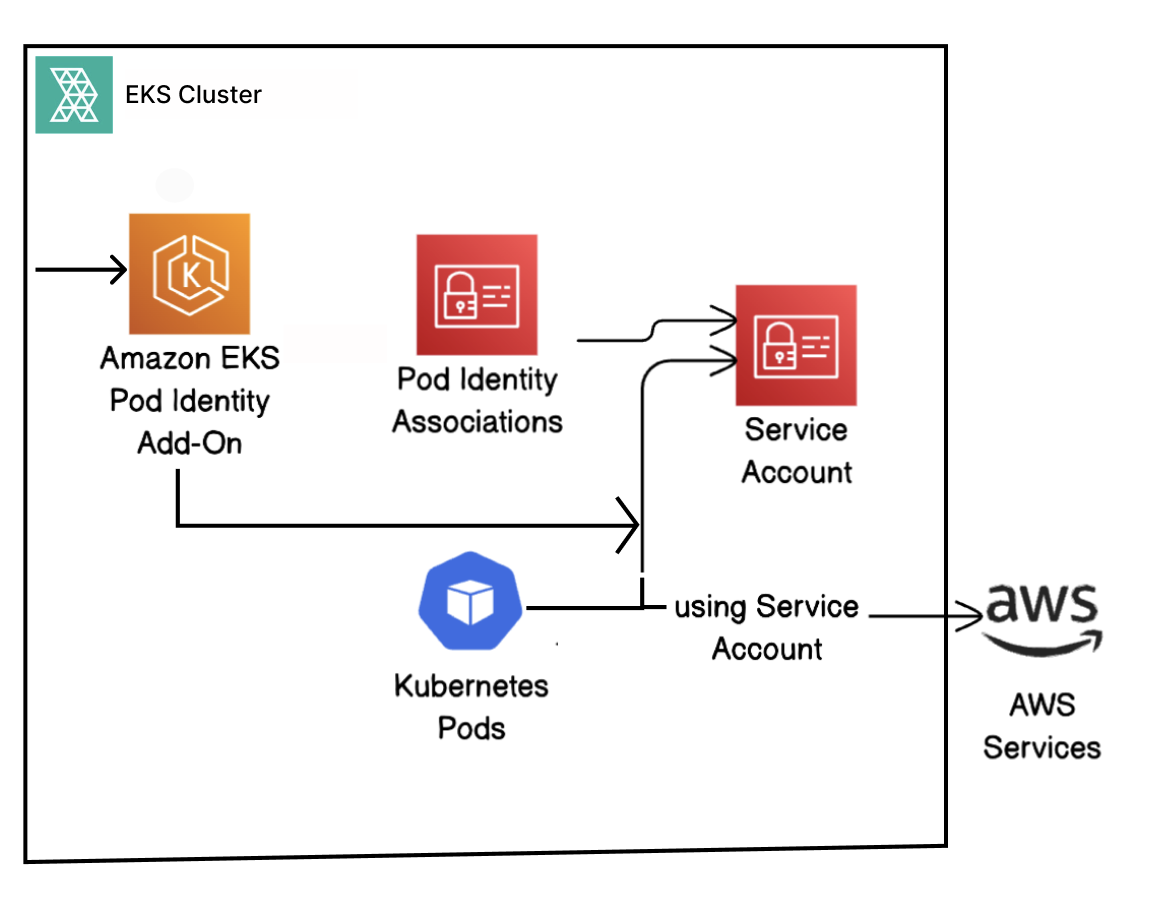
Install the Amazon EKS Pod Identity Agent Add-On on Your Amazon EKS Cluster Managed through Rafay.¶
The Amazon EKS Pod Identity Agent is a component that runs as a daemonset in a Cluster, enabling Kubernetes pods on Amazon EKS to securely obtain temporary AWS IAM credentials. You can install this managed add-on during Day 0 (at the time of cluster creation) or in Day 2 (on an existing cluster).
Day 0 Installation of Amazon EKS Pod Identity Add-On
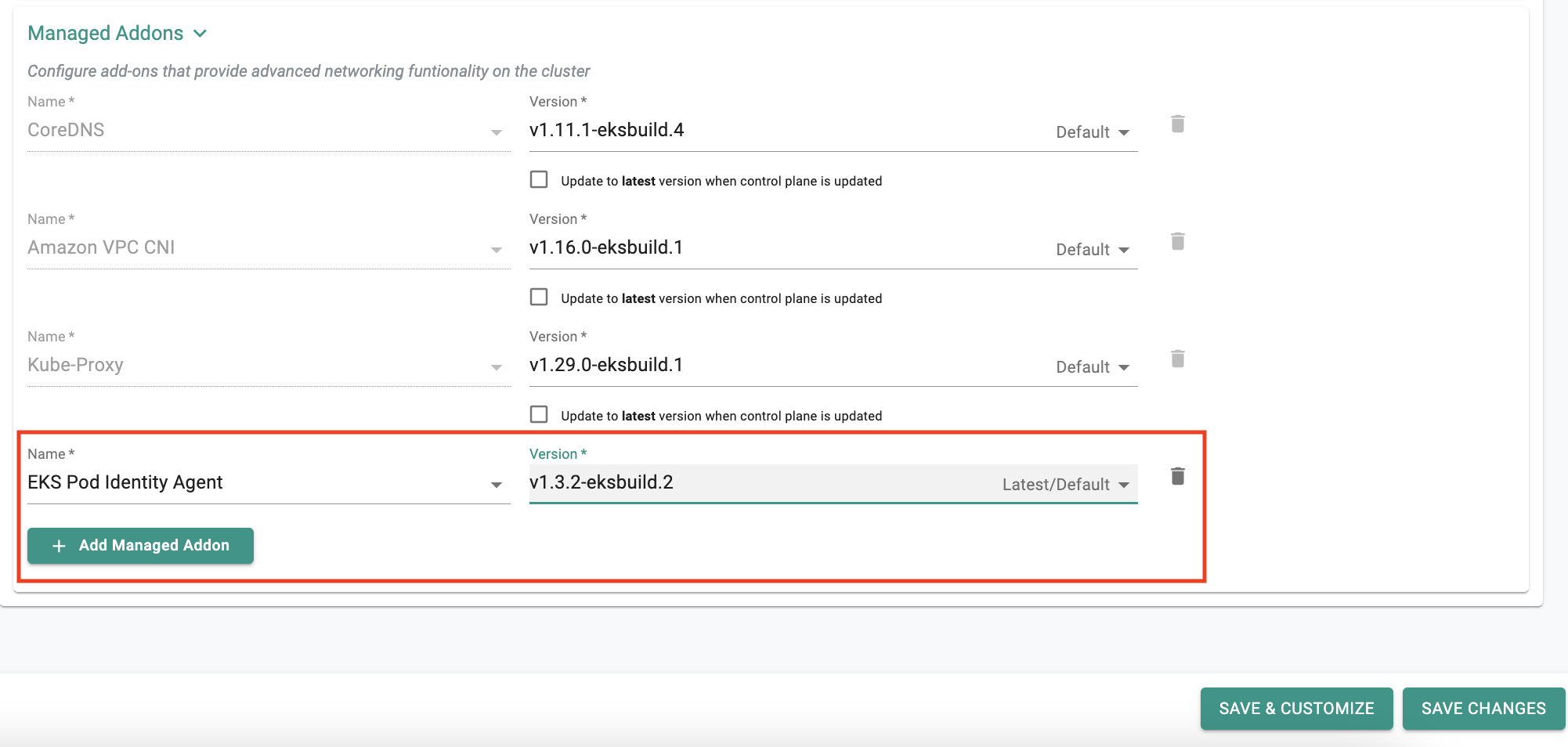
When creating an Amazon EKS cluster using Rafay's RCTL CLI or GitOps SystemSync on Day 0, you can deploy the Pod Identity Agent (PIA) add-on along with PIA associations as shown below :
kind: Cluster
metadata:
labels:
cli: eks
name: demo-eks
project: defaultproject
spec:
blueprint: minimal
blueprintversion: 2.10.0
cloudprovider: gopi-eks
cniprovider: aws-cni
proxyconfig: {}
type: eks
---
addons:
- name: coredns
version: v1.10.1-eksbuild.4
- name: vpc-cni
version: v1.16.0-eksbuild.1
- name: kube-proxy
version: v1.28.2-eksbuild.2
- name: eks-pod-identity-agent
version: v1.3.2-eksbuild.2
- name: aws-ebs-csi-driver
version: latest
apiVersion: rafay.io/v1alpha5
iam:
podIdentityAssociations:
- createServiceAccount: true # (true|false)
namespace: qa
roleARN: <role arn>
serviceAccountName: <sa name>
tags:
env: qa
kind: ClusterConfig
managedNodeGroups:
- amiFamily: AmazonLinux2
desiredCapacity: 1
iam:
withAddonPolicies:
autoScaler: true
instanceTypes:
- t3.xlarge
maxSize: 2
minSize: 0
name: ng-72f4dcef
version: "1.28"
volumeSize: 80
volumeType: gp3
metadata:
name: eks-demo122
region: us-west-2
tags:
email: [email protected]
env: qa
version: "1.28"
vpc:
cidr: 192.168.0.0/16
clusterEndpoints:
privateAccess: true
publicAccess: false
nat:
gateway: Single
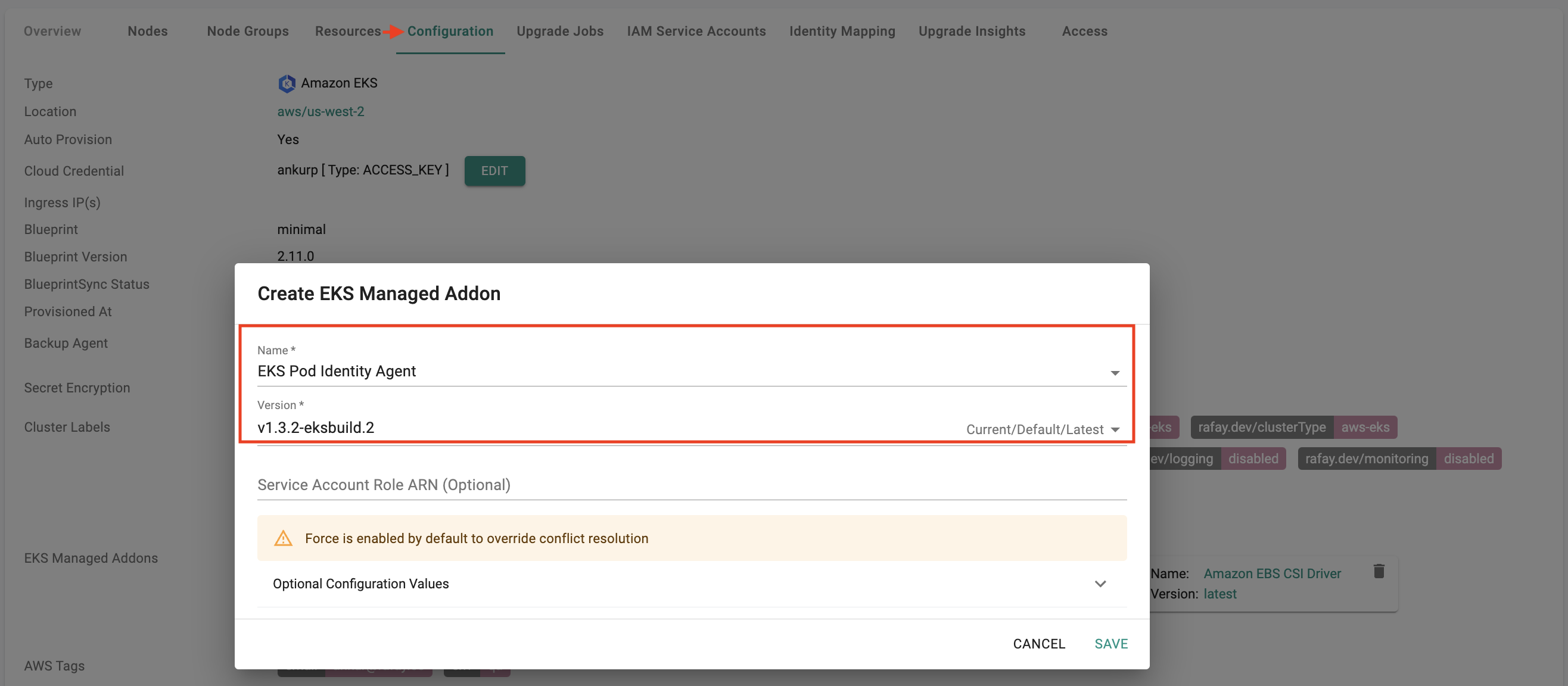
Day 2 Installation of Amazon EKS Pod Identity Add-On and Associations
If you have an existing EKS cluster provisioned and managed using Rafay, you can easily add Pod Identity to it on day-2. Some examples shown below.
kind: Cluster
metadata:
labels:
cli: eks
name: demo-eks
project: defaultproject
spec:
blueprint: minimal
blueprintversion: 2.10.0
cloudprovider: gopi-eks
cniprovider: aws-cni
proxyconfig: {}
type: eks
---
addons:
- name: coredns
version: v1.10.1-eksbuild.4
- name: vpc-cni
version: v1.16.0-eksbuild.1
- name: kube-proxy
version: v1.28.2-eksbuild.2
- name: eks-pod-identity-agent
version: v1.3.2-eksbuild.2
- name: aws-ebs-csi-driver
version: latest
apiVersion: rafay.io/v1alpha5
iam:
podIdentityAssociations:
- createServiceAccount: true # (true|false)
namespace: qa
roleARN: <role arn>
serviceAccountName: <sa name>
tags:
env: qa
kind: ClusterConfig
managedNodeGroups:
- amiFamily: AmazonLinux2
desiredCapacity: 1
iam:
withAddonPolicies:
autoScaler: true
instanceTypes:
- t3.xlarge
maxSize: 2
minSize: 0
name: ng-72f4dcef
version: "1.28"
volumeSize: 80
volumeType: gp3
metadata:
name: eks-demo122
region: us-west-2
tags:
email: [email protected]
env: qa
version: "1.28"
vpc:
cidr: 192.168.0.0/16
clusterEndpoints:
privateAccess: true
publicAccess: false
nat:
gateway: Single
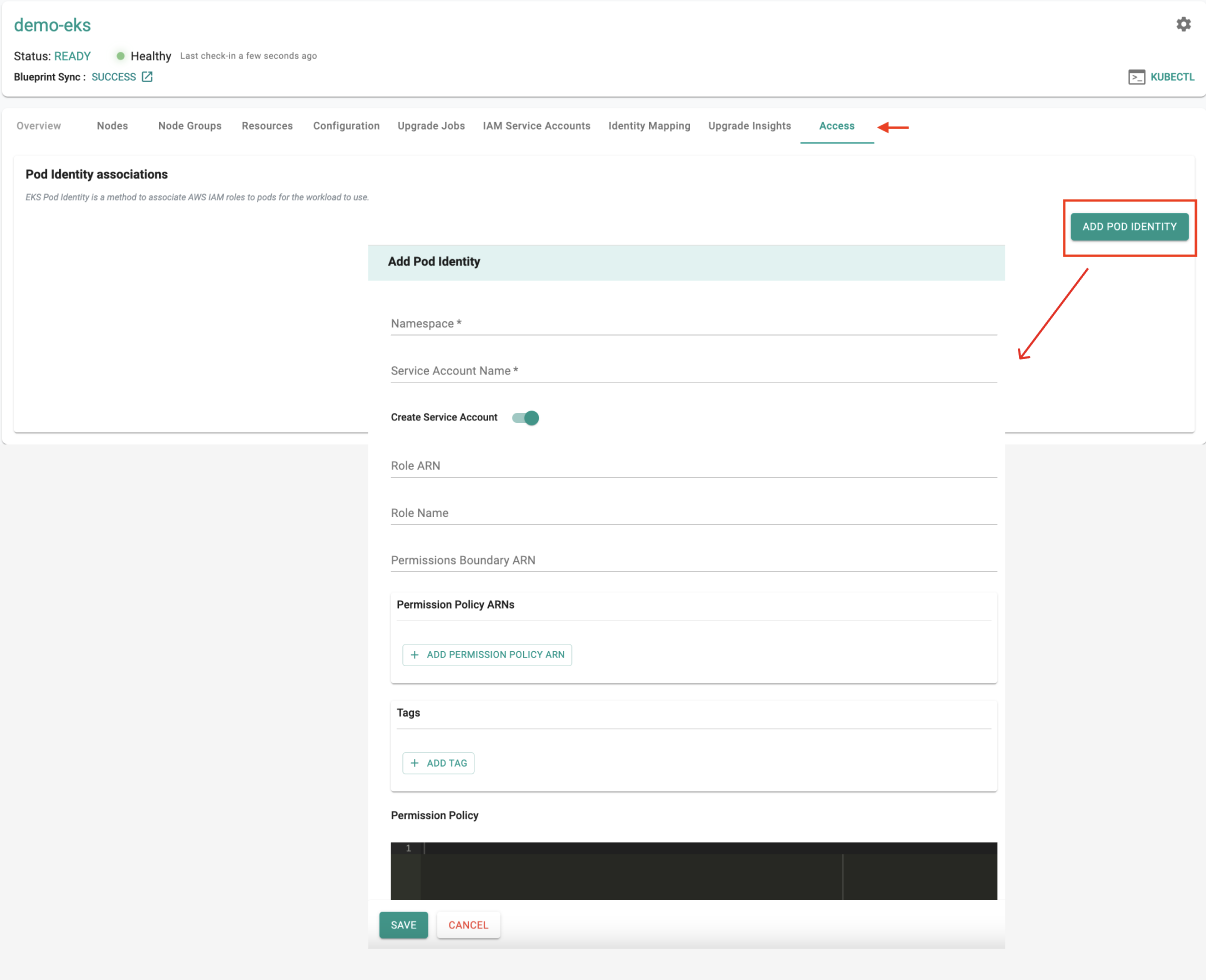
In addition to deploying and configuring Pod Identity associations using Rafay's console, RCTL CLI and GitOps, you can manage their lifecycle as a separate resource using Rafay's Terraform Provider. This approach allows for version control and automation of your IAM roles and service accounts, making it easier to maintain and update configurations across multiple environments.
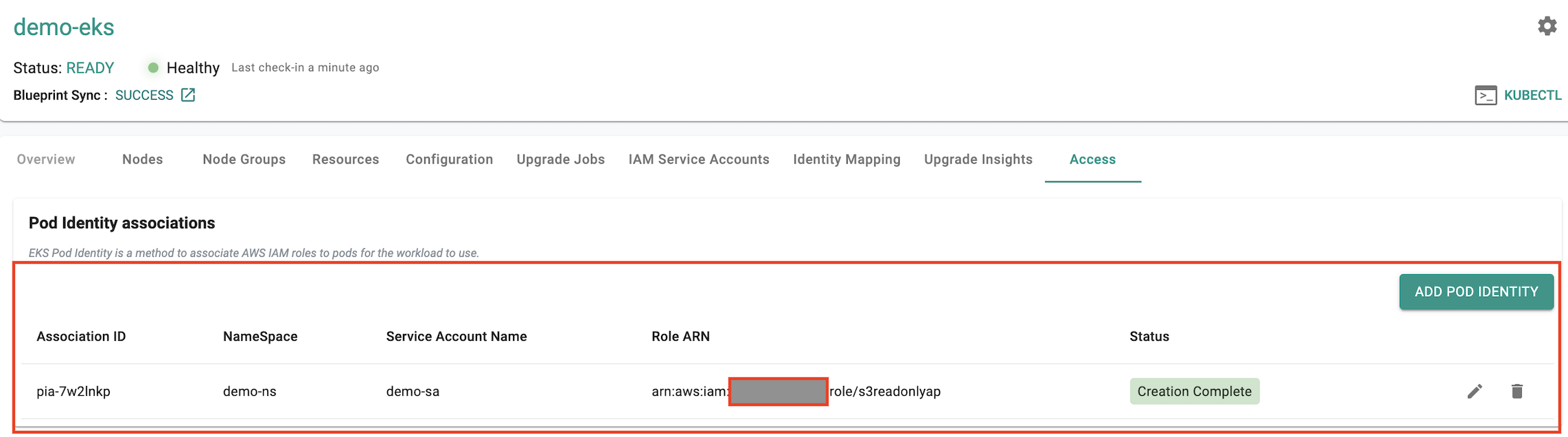
Once you create the associations with the appropriate roles, policies, and service account configurations, an entry for the association will appear in the Access tab. This entry will enable the creation of a service account that Kubernetes pods can use to securely interact with AWS services.

Note
For the lifecycle of Pod Identity associations, ensure that the following IAM permissions are added for the role or user used in the cloud credentials for the lifecycle of a cluster:
eks:CreatePodIdentityAssociationeks:DescribePodIdentityAssociationeks:DeletePodIdentityAssociationeks:UpdatePodIdentityAssociationeks:ListPodIdentityAssociations
Conclusion¶
Amazon EKS Pod Identity significantly simplifies the management of IAM roles for applications running on Amazon EKS managed through the Rafay platform. With this feature, you can easily reuse IAM roles across multiple EKS clusters without the need to update the role trust policy each time a new cluster is created. This not only streamlines the process but also enhances security by reducing the potential for misconfigurations. By associating IAM roles directly with Kubernetes service accounts, applications can seamlessly obtain the necessary permissions to interact with AWS services.
Summary¶
In Part 3 of this blog, I will discuss how you can seamlessly migrate your existing IRSA to Pod Identity using Rafay.
