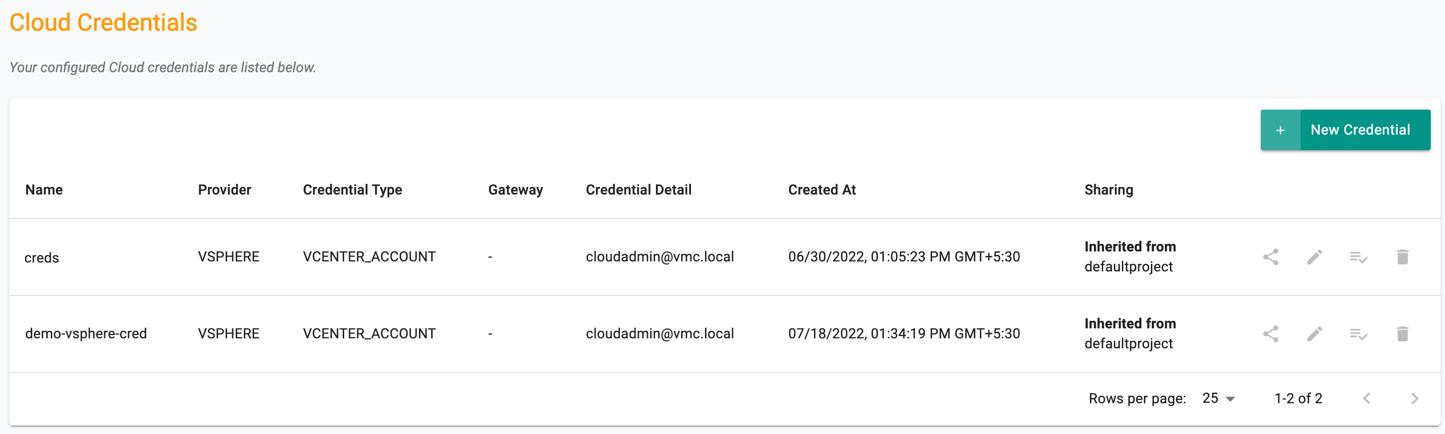
Credentials for VMware¶
With the Controller, you can fully automate the provisioning and ongoing lifecycle management of vSphere clusters in all supported VMware regions.
With auto-provisioning, you can have a cluster operational in just a few clicks. To do this, you need to provide credentials that allow programmatic access to vSphere vCenter
Create Cloud Credential¶
- Login to the Console and select Cloud Credentials under Infrastructure
- Click New Credential and provide a unique name
- Select the Type Cluster Provisioning and Provider VSPHERE
- Select the required Gateway and enter the vCenter server URL
- Provide the vCenter Username and Password
- Click Save
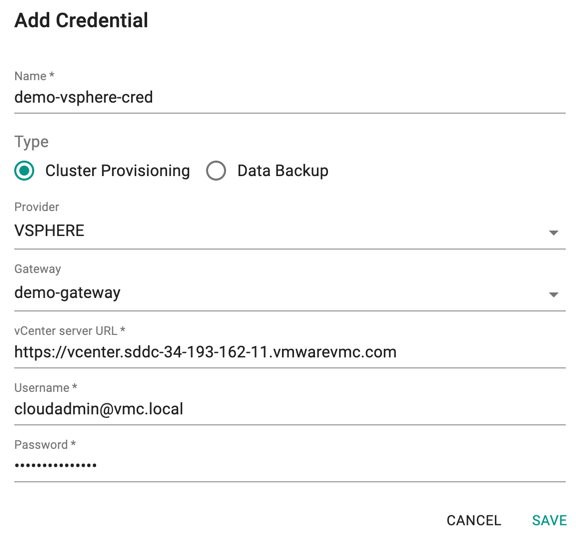
On successful creation, you can view the credential listed as shown below
Existing Credential¶
Navigate to the "Cluster->Configuration" tab to view the "cloud credential" currently being used by the cluster. Both the "name" and "type" will be displayed.
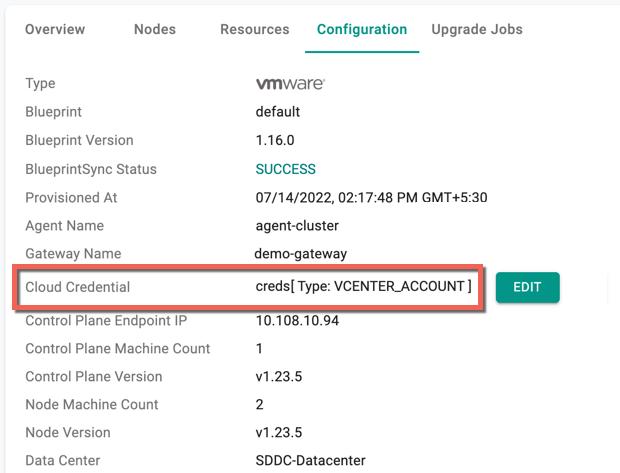
Replace Credential¶
To swap the existing cloud credential with a new one, follow the steps below
- Create the new cloud credential
- Navigate to the "Cluster->Configuration" tab
- Click on "Edit" and select the replacement cloud credential from the dropdown
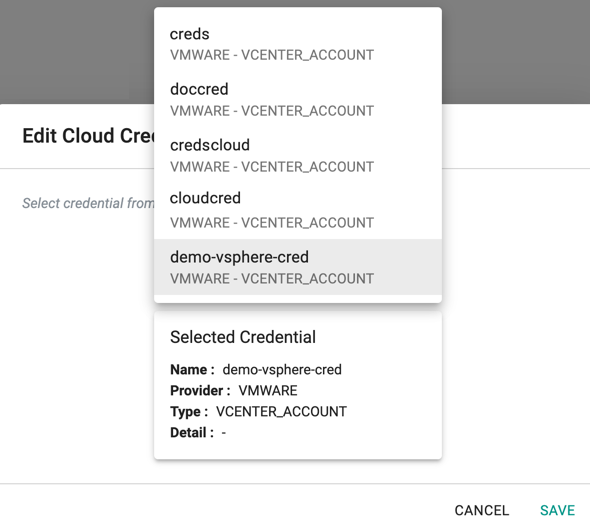
Any subsequent operations on the managed cluster will be performed using the "new cloud credential".
Sharing¶
Organizations can create and use "unique" cloud credentials per project. This approach can be useful if different cloud provider accounts need to be used in every project. This helps with "billing" and "isolation". However, this approach may not be practical for scenarios where the organization's security policies may require "centralization" of cloud credentials. For scenarios like this, organizations can "share" their cloud credentials with selected or all projects.
- Click on the "share" menu option
- Select the projects you would like to share the cloud credential with
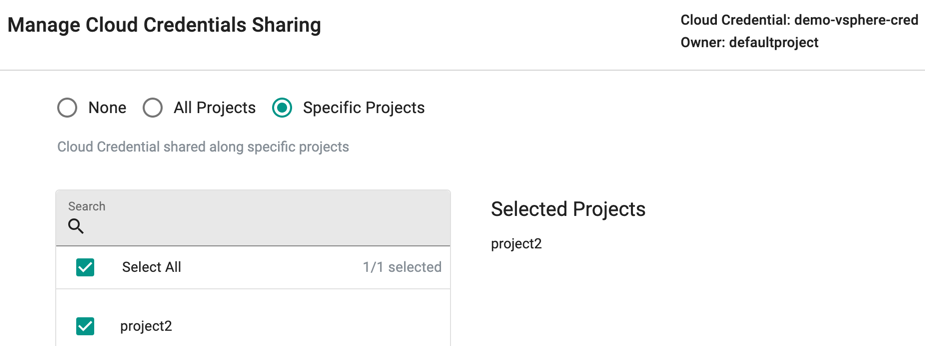
The downstream projects that "inherit" the shared cloud credential can view and use the inherited cloud credentials. But, they are not allowed to edit/delete them.