Overview
In addition to lifecycle of k8s workloads, the Infrastructure Provisioner stage in a pipeline can be used to manage the lifecycle of infrastructure as well. Currently, Terraform by Hashicorp is supported as a "provider".
Infrastructure Provisioners are "scoped" to a specific project and are bound by associated RBAC rules. Users can have "as many" infrastructure provisioners in a project as they require. Once configured, the infrastructure provisioner can be executed on a managed agent running in a cluster in the customer's infrastructure to provision/update/deprovision infrastructure based on the specified Terraform code.
All the operations described below can also be specified declaratively in YAML files using the RCTL CLI.
Terraform¶
Terraform - Is an open-source infrastructure as code software tool that provides a consistent CLI workflow to manage hundreds of cloud services. - It codifies cloud APIs into declarative configuration files. - It is a tool for building, changing, and versioning infrastructure safely and efficiently. - It can manage existing and popular service providers as well as custom in-house solutions.
Config Files¶
Configuration files describe to Terraform the components needed to run a single application or your entire datacenter. Terraform generates an execution plan describing what it will do to reach the desired state, and then executes it to build the described infrastructure. As the configuration changes, Terraform is able to determine what changed and create incremental execution plans which can be applied.
State Files¶
Terraform must store state about your managed infrastructure and configuration. This state is used by Terraform to map real world resources to your configuration, keep track of metadata, and to improve performance for large infrastructures. The primary purpose of Terraform state is to "store bindings" between objects in a remote system and resource instances declared in your configuration. When Terraform creates a remote object in response to a change of configuration, it will record the identity of that remote object against a particular resource instance, and then potentially update or delete that object in response to future configuration changes.
Create¶
Under GitOps->Infra Provisioner, click on "New Infrastructure Provisioner" and provide it a name. The remaining details are split into three logical areas described below
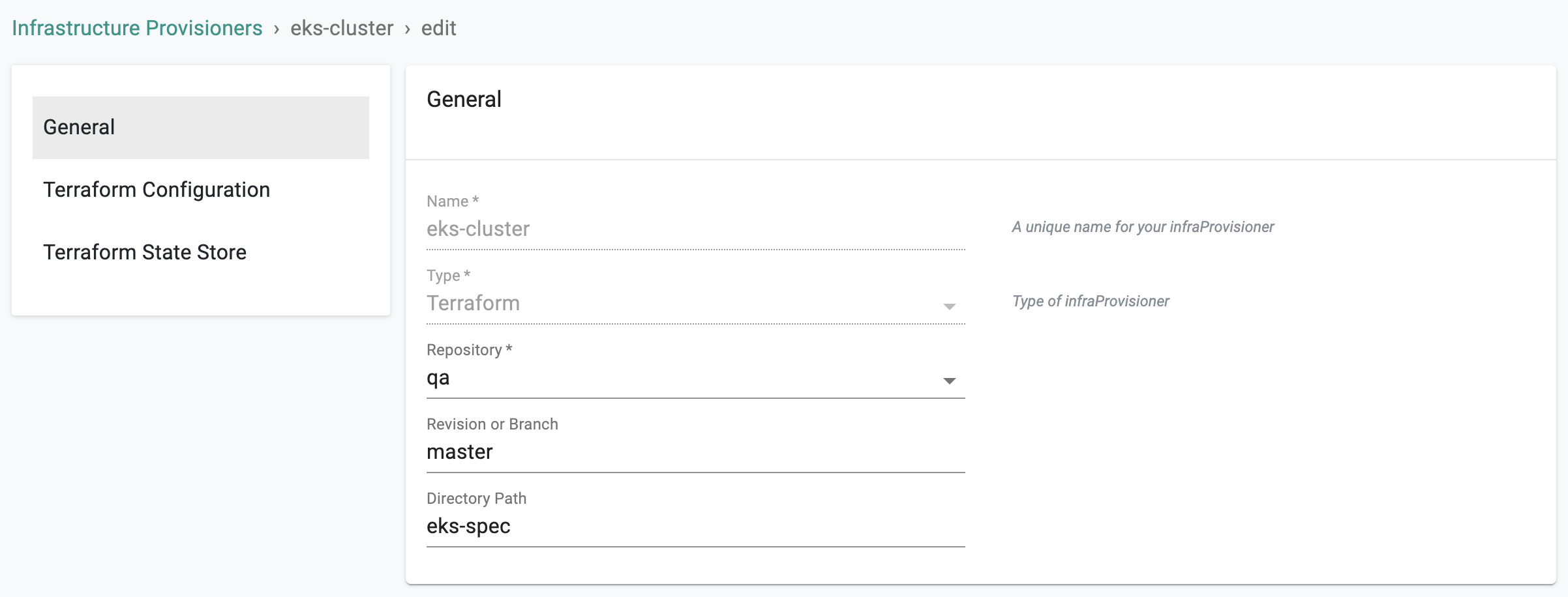
General¶
In this section, we will specify where the infra provisioner can find your Terraform code.
- Select the repository (both Internet facing and Private, Behind Firewall options are supported)
- Specify the revision/branch
- Specify the directory path for the Terraform code
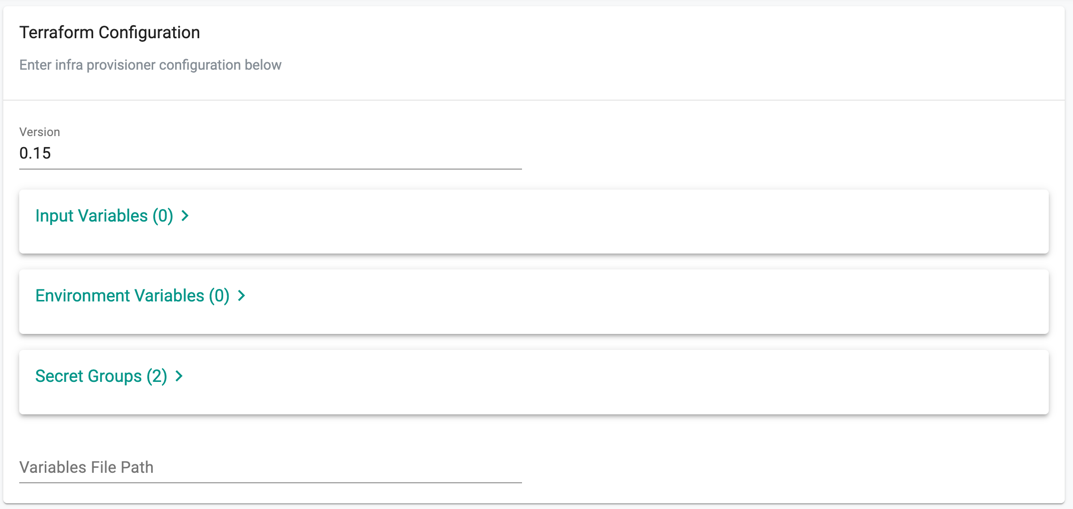
Terraform Config¶
In this section, we will specify the input configuration for Terraform.
- Specify a valid Terraform version (e.g. 0.15). This version number is used to construct the Terraform CLI download URL based on the pattern: https://releases.hashicorp.com/terraform/%s/terraform_%s_linux_amd64.zip
- If needed, specify Input Variables for Terraform
- If needed, specify Environment Variables for Terraform
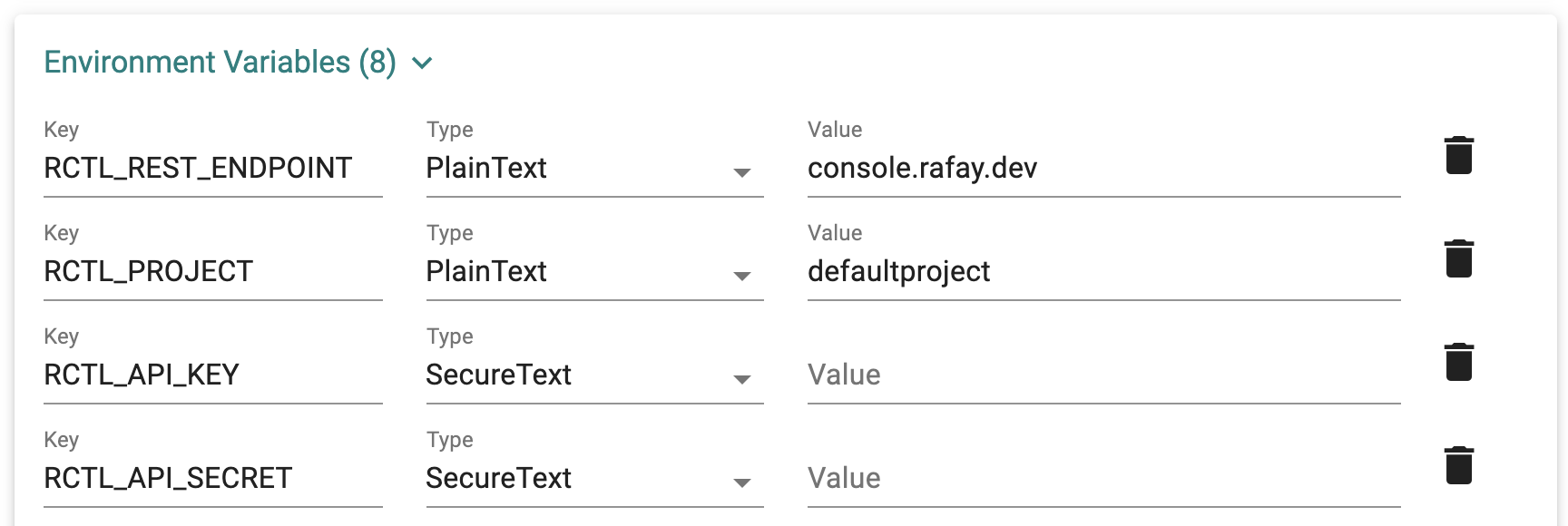
When a user does not wish to use the AWS key and secret in the infra provisioner environment variables to provision your infrastructure in AWS, perform the docker agent work-around as below:
- Create a gitops docker agent in the controller where the docker-compose file and instructions to install are available
- Install this docker agent to one of the EC2 instances
- Ensure the Instance role attached to this EC2 instance has the permission to create the AWS resources that are required from the terraform code
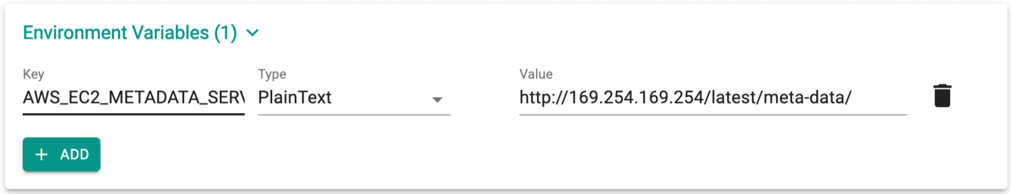
- In the Infra Provisioner, provide an environment variable with key AWS_EC2_METADATA_SERVICE_ENDPOINT and value http://169.254.169.254/latest/meta-data/ as shown below
- If needed, specify Secret Groups for Terraform

Terraform State¶
In this section, we will specify details for Terraform state file management.
- If needed, specify Variables for Terraform State
- If needed, specify Environment Variables for Terraform
View¶
Administrators can view the list of available infrastructure provisioners in the project
Edit¶
Administrators can edit and update existing infrastructure providers by clicking on Edit and then Save the changes.
Delete¶
Administrators can delete existing infrastructure providers by clicking on Delete.
Use Infra Provisioner¶
Once created, an infra provisioner can be used in a Stage in a pipeline.
- Provide a unique name for your stage
- Select "Infrastructure Provisioner" for Action
- Select the Infra Provisioner that you created
- Specify the Git revision
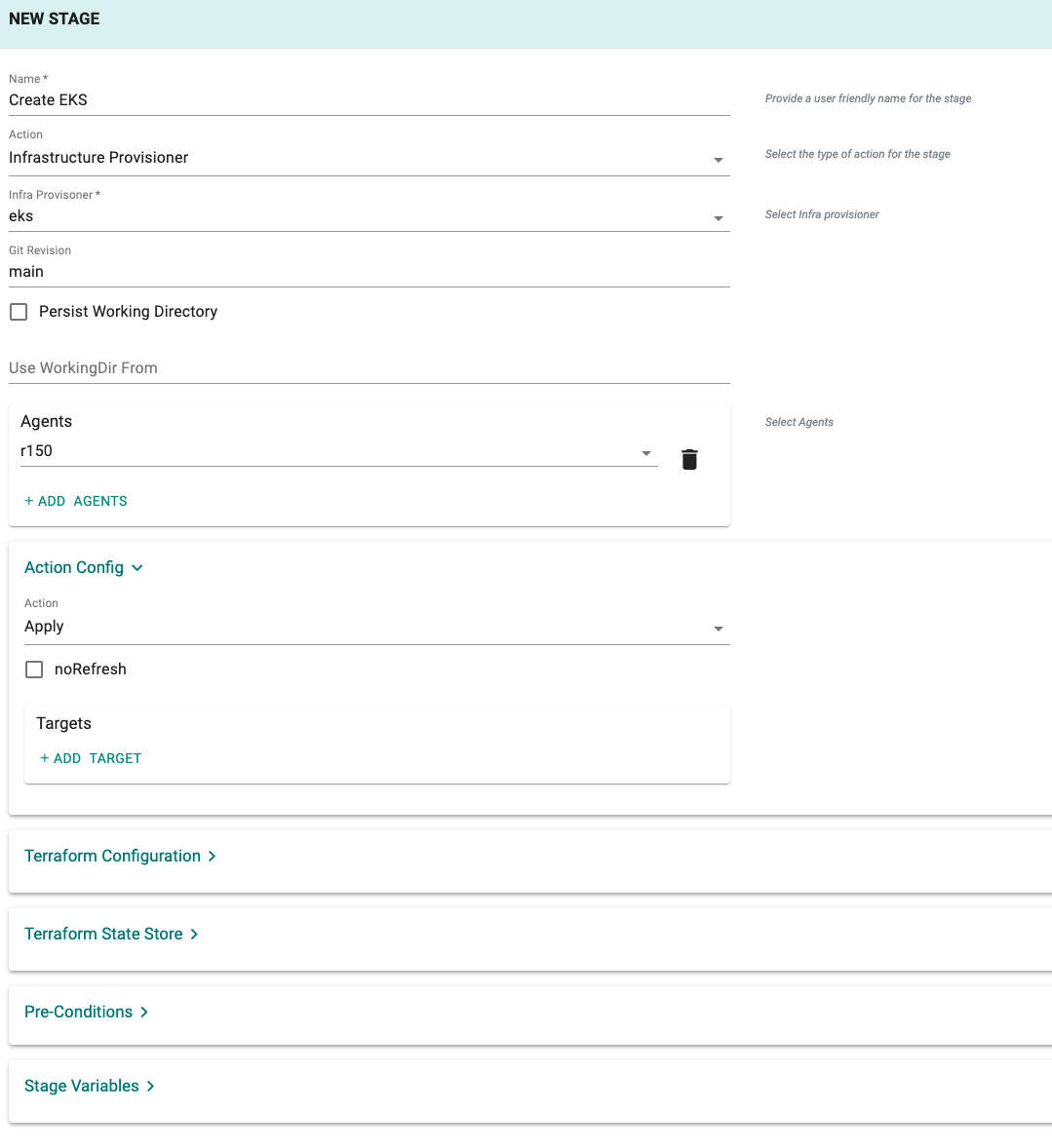
Agents¶
Select the agent(s) where the Terraform code will be executed. These managed agents run on Kubernetes clusters managed by the controller.
Action Config¶
Terraform supports many types of actions "Plan", "Apply" and "Destroy". Select which of these actions you would like to perform in this stage.
Overrides¶
Specify overrides if required for the following configuration items:
- Terraform Config
- Terraform State Store
- Pre-Conditions
- Stage Variables